
How to apply the principles and methods of digital forensics within the cloud environment to investigate a security incident?
Cloud forensics seeks to apply the principles and methods of digital forensics within the cloud environment to investigate any security incident. To obtain digital evidence in a cloud environment, investigators must know the data location and the access level exercised by a specific organization on that data.
Cloud forensics has many uses:
- Investigation
Cloud forensics helps in finding the source of different cloud-based crimes and solving organized cloud crimes, policy violations in a public environment, and suspicious activities in a cloud environment. In the investigation process, all sources, including manual and mechanical, are analyzed and the results are revealed. This helps the clients and service providers to secure their cloud services.
- Troubleshooting
Cloud forensic techniques assist users in troubleshooting by determining the data and hosts that are physically and virtually present in a cloud environment. They allow users to find and resolve any errors or security issues in the cloud. They help in understanding the trends of past security attacks to tackle any incident in the future.
- Log monitoring
Cloud forensic techniques include processes for generating, storing, analyzing, and correlating the massive volumes of log data created within a cloud environment. These data help the users and service providers to audit, analyze, and calculate various aspects of the cloud environment; they also help security officials in checking whether a cloud system complies with the regulatory standards.
- Data and system recovery
Cloud forensics involves recovery procedures that help forensic practitioners in recovering lost, accidentally deleted, corrupted, and inaccessible data. It also enables the data acquisition of cloud systems and the creation of a forensic copy of the data that can be used by the service providers as back up; forensic experts can use this copy as evidence in the court of law.
- Due diligence/regulatory compliance
Cloud forensics also deals with the security aspects of an organization in securing critical data, maintaining necessary records for auditing purposes, and notifying the concerned team when any suspicious activity is reported; for instance, if private data have been misused or exposed. It also helps in finding the sections that miss a regulatory compliance and fixes.
Cyber Kill Chain
Security Center’s threat protection includes fusion kill-chain analysis, which automatically correlates alerts in your environment based on cyber kill-chain analysis, to help you better understand the full story of an attack campaign, where it started and what kind of impact it had on your resources. Security Center’s supported kill chain intents are based on the MITRE ATT&CK™ framework.
As illustrated below, the typical steps that trace the stages of a cyberattack

- Reconnaissance: The observation stage where attackers assess your network and services to identify possible targets and techniques to gain entry.
- Intrusion: Attackers use knowledge gained in the reconnaissance phase to get access to a part of your network. This often involves exploring a flaw or security hole.
- Exploitation: This phase involves exploiting vulnerabilities and inserting malicious code onto the system to get more access.
- Privilege Escalation: Attackers often try to gain administrative access to compromised systems so they can get access to more critical data and move into other connected systems.
- Lateral Movement: This is the act of moving laterally to connected servers and gain greater access to potential data.
- Obfuscation / Anti-forensics: To successfully pull off a cyberattack, attackers need to cover their entry. They will often compromise data and clear audit logs to try to prevent detection by any security team.
- Denial of Service: This phase involves disruption of normal access for users and systems to keep the attack from being monitored, tracked, or blocked.
- Exfiltration: The final extraction stage: getting valuable data out of the compromised systems.
Threat Hunting Tools and Methodology
To ensure maximum visibility of the attack chain, hunters use data sourced from proprietary incident response tooling for point-in-time deep scanning on endpoints, as well as bespoke forensic triage tools on devices of interest.
For point-in-time deep scanning, for forensic investigations uses:
- Proprietary incident response tooling for Windows and Linux.
- Forensic triage tool on devices of interest.
- Microsoft Azure Active Directory (Azure AD) security and configuration assessment.

For continuous monitoring:
- Microsoft Sentinel — Provides centralized source of event logging. Uses machine learning and artificial intelligence.
- Microsoft Defender for Endpoint — For behavioral, process-level detection. Uses machine learning and artificial intelligence to quickly respond to threats while working side-by-side with third-party antivirus vendors.
- Microsoft Defender for Identity — For detection of common threats and analysis of authentication requests. It examines authentication requests to Azure AD from all operating systems and uses machine learning and artificial intelligence to quickly report many types of threats, such as pass-the-hash, golden and silver ticket, skeleton key, and many more.
- Microsoft Defender for Cloud Apps — Cloud Access Security Broker (CASB) that supports various deployment modes including log collection, API connectors, and reverse proxy. It provides rich visibility, control over data travel, and sophisticated analytics to identify and combat cyberthreats across all your Microsoft and third-party cloud services.
- Deep scan includes proprietary endpoint scanners such as ASEP, Fennec, LIFE, and FoX
- Enterprise data includes Active Directory Configuration and Antivirus logs.
- Global telemetry includes the Intelligent Security Graph, the largest sensor network in the world.
Continuous monitoring includes the following:
- Microsoft Defender for Office 365, which monitors spoofing impersonation, and content analysis.
- Microsoft Defender for Cloud Apps, which monitors app discovery, access management, and data loss prevention.
- Microsoft Defender for Endpoint, which monitors exploitation, installation, and command and control channel.
- Microsoft Defender for Identity, which monitors reconnaissance, lateral movement, and domain dominance.
- Microsoft 365 Defender, Microsoft Sentinel, and Microsoft Defender for Cloud, which include advanced hunting, alerting, and correlation across data sources.

This is example Hunting through the Attach chain:

Starting with IOCs (“known bads”)
The hunting cycle starts with hunting for indicators or “known bads,” ranging from the smallest unit of indicators to behavioral indicators that may define the actor.
An incident response investigation is more manageable when you start off with an initial indicator of compromise (IOC) trigger, or a “known bad,” to take you to any additional findings. We typically begin with data reduction techniques to limit the data we’re looking at. One example is data stacking, which helps us filter and sort out forensic artifacts by indicator across the enterprise environment until we’ve determined that several machines across the same environment have been confirmed with that same IOC trigger. We then enter the hunting flow and rinse and repeat this process.

When a security incident is detected on the Azure cloud platform, investigators must examine the log data collected from various sources. If a VM is found to be affected, it is important to take a snapshot of the OS disk of the VM for further investigation. This section discusses the forensic acquisition methodology of an Azure VM and discusses an assumed scenario to divide the whole process into multiple steps.
Virtual machine acquisition on the Azure cloud platform includes the following steps:
- Create a snapshot of the OS disk of the suspect VM via Azure portal or Azure CLI
- Copy the snapshot to a storage account under different resource groups where it can be stored for forensic analysis
- Delete the snapshot from the source resource group and create a backup copy
- Mount the snapshot onto the forensic workstation
DFIR Scenario:
In my environment I created two resource group in the same Azure Subscription:
- Uros-PROD for production enviroment
- SECURITY-UROS for DFIR investigations
- Under Uros-PROD resource group there is VM called Ubuntu-Uros which is suspected to be compromised
As a forensics investigator I need to take snapshot of the OS disk of the suspected VM Ubuntu -Uros for further DIFR investigations:

Step 1: Create Snapshot of the OS disk of the affected VM in Azure Portal
Shut down th VM Ubuntu-Uros whose snapshot needs to be created

Step 2: Locate Ubuntu Ubuntu-Uros_OsDisk from Uros-PROD resource group

Step 3: Click on Snapshot button

Step 4: Create snapshot of the OS disk on the Affected VM Ubuntu -UrosGive desired name of OS snapshot (urosubuntudisksnap)storage type standard HDD
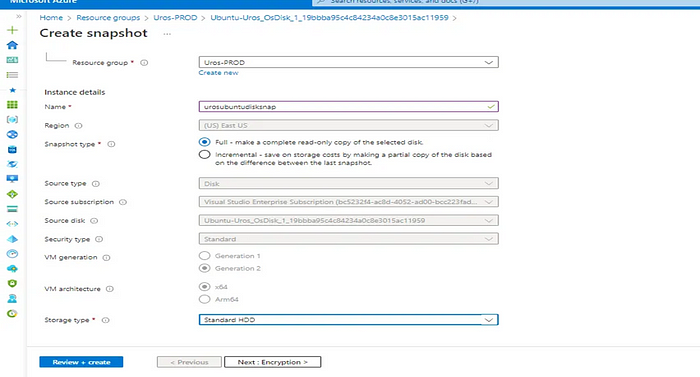
Step 5: urosubuntudisksnap snapshot is successfully created

Step 6: Mount the snapshot onto the forensic workstation:
Open File Explorer from the Start Menu or press Win+E key togetherSelect This PC from the left-side menu, click on Computer, and select Map Network DriveSelect the drive letter and provide the UNC path in file shareIf prompted, provide the storage account name as username and storage key as passwordThe file share chfishare is now mounted under Network Locations . Double-click on the mounted share to view the dd file

Step 7: Analyze the Snapshot via Autopsy
Once the file share containing the disksnapshot.dd file is mounted on the Forensic workstation, you can conduct forensic examination on the contents of the OS disk of the affected VM via tools like Autopsy

RECOMMENDATIONS AND BEST PRACTICES:
Recommendations for devices
Active Directory Hardening
You should review the Active Directory Administrative Tier model (0/1/2), Restrict Service Accounts from interactive logins.

Use MSA or GMSA for Service Accounts
Standardize DCs and reduce attack surface
Microsoft Defender for Endpoint
Enroll 100% of devices in Microsoft Defender for Endpoint
Actively monitor alerts and quickly take action on issues in the console
Leverage Microsoft Threat Experts for help monitoring advanced attacks
Regularly review Threat and Vulnerability Management and follow remediation steps, starting with most critical to your organization
Patching
Implement a comprehensive patching strategy across all systems, for both Microsoft and 3rd party products. This is critical.
Windows 10 Hygiene
Tighten up Windows 10 build to N-1.
Enable Credential/Device/Exploit Guard, Windows Hello for Business, SmartScreen, Application Control, Controlled Folder Access, Attack Surface Reduction, BitLocker, Secure Boot, etc.
Windows Firewall
Ensure this is enabled on 100% of computers via Group Policy. This greatly reduces lateral movement attack surface
Block all the incoming connection on the clients (manage the exceptions for Help Desk access)
Recommendations for identity
Manage Legacy protocols
Inventory & Disable SMBv1
Inventory & Disable NTLM
Inventory & Discontinue use of TLS 1.0 and 1.1 (EOL ‘Spring 2021’)
Update all services & apps which use SMTP, Telnet, FTP, IMAP, etc. to modern non-clear-text alternatives. This is required to disable Legacy Authentication in Office 365, which is required for Conditional Access
Strong Authentication
A username and password is no longer enough. Use technologies such as Passwordless, Hello for Business, FIDO, Azure AD MFA or OATH tokens to enforce Strong Authentication for all signings.
Centralize Logging
Ensure that sign in data flows to a central location for detailed analysis and enrichment
Just-in-time administration
Where possible, enforce just-in-time access for administration, using solutions like Privileged Identity Management for Azure AD or Privileged Access Management for Active Directory

Credential Hygiene
Continue Credential Hygiene Best Practices
www.aka.ms/tier0 for reference materials
Recommendations for access
Risk based access
Consider using the risk level of users and devices as a condition for accessing corporate systems
Block access or require higher level of confidence for users and/or devices based on risky activities
Requires Azure AD Identity Protection and / or Intune and MDE enrolment
Remote Tools & VPN
Remote access tools were identified. Ensure that 100% of these are managed & monitored for legitimate usage
Ensure VPN clients are legitimate & monitored, and MFA is required
Monitor & Audit MSSP
Perform regular audits of any external vendors management and activity
Privileged Access Workstation (PAW)
Securing privileged access is a critical first step to establishing security assurances for business assets in a modern organization. The security of most or all business assets in an IT organization depends on the integrity of the privileged accounts used to administer, manage, and develop.
This above figure shows how reversing the control relationship and accessing user apps from an admin workstation gives the attacker no path to the targeted object. The user jump box is still exposed to risk so appropriate protective controls, detective controls, and response processes should still be applied for that internet-facing computer.

Securing privileged access is a critical first step to establishing security assurances for business assets in a modern organization. The security of most or all business assets in an IT organization depends on the integrity of the privileged accounts used to administer, manage, and develop.
Plan deployment of Privileged Admin Workstation (PAW) for EA/DA T0, T1, and Azure admins.
Monitor T0 accounts and audit usage regularly.
Recommendations for cloud
User Entity Behavioral Analytics (UEBA)
Use Cloud App Security and Azure AD Identity Protection to identify anomalous user activity.
Manage and respond to alerts regularly to help train the systems.
Azure Security Center
Monitor and manage IaaS and PaaS security configurations to protect cloud workloads. Use Insights and Recommendations to prioritize and plan remediation activities
Azure Monitor + Defender for Cloud + Sentinel+XDR
Microsoft Sentinel is a cloud-native SIEM tool; Microsoft 365 Defender provides XDR capabilities for end-user environments (email, documents, Microsoft Teams, identity, apps, and endpoint); and Microsoft Defender for Cloud provides XDR capabilities for infrastructure and multicloud platforms including virtual machines, databases, containers, storage, and IoT. Altogether, the security operations team gets a fully integrated solution to prevent, detect, respond to, and protect against attacks.

Microsoft 365 security center
Benefit from a combined incident queue, correlation of signals across cloud services and configuration management for multiple platforms in one place.
Microsoft Defender for Office 365
Use behavioral analysis of emails, attachments and files to protect Office 365 from zero day or polymorphic threats.
Anti-Phishing policies help protect against user or domain impersonation.
Regularly review and respond to alerts in the Microsoft 365 security center and train end-users with Attack Simulation training modules.
SMB — Preventing SMB traffic
Because SMB is a remote file system, it requires protection from attacks where a Windows computer might be tricked into contacting a malicious server running inside a trusted network or to a remote server outside the network perimeter. Firewall best practices and configurations can enhance security preventing malicious traffic from leaving the computer or its network.
Impact of changes
Blocking connectivity to SMB may prevent various applications or services from functioning. For a list of Windows and Windows Server applications and services that may stop functioning, review Service overview and network port requirements for Windows.

Weak Passwords
Enable Azure AD Password Protection
Detects and blocks known weak passwords and their variants and can also block additional weak terms that are specific to your organization.
On-premises deployment of Azure AD Password Protection uses the same global and custom banned password lists that are stored in Azure AD and does the same checks for on-premises password changes as Azure AD does for cloud-based changes.
These checks are performed during password changes and password reset events against on-premises Active Directory Domain Services (AD DS) domain controllers.

Password Leak
Azure Identity Protection
Azure AD works by calculating a user risk level for each user.
The risks identified by Azure AD Identity Protection are:
- Leaked credentials
- Impossible travel to atypical locations
- Sign-ins from infected devices
- Sign-ins from anonymous IP addresses
- Sign-ins from IP addresses with suspicious activity
- Signs in from unfamiliar locations

Companies must guarantee that digital evidence they provide in response to legal requests demonstrates a valid Chain of Custody (CoC) throughout the evidence acquisition, preservation, and access process. To ensure a valid CoC, digital evidence storage must demonstrate adequate access control, data protection and integrity, monitoring and alerting, and logging and auditing.