
Microsoft has introduced the Microsoft Security Copilot agents, along with new protections for AI. The six new agentic solutions empower security teams to autonomously manage high-volume security and IT tasks by seamlessly integrating with Microsoft Security solutions.
Specifically designed for security purposes, these agents learn from feedback, adapt to workflows, and operate securely within Microsoft’s Zero Trust framework. By putting security teams in full control, these agents enhance response times, prioritize risks, and improve efficiency, ultimately supporting proactive protection and bolstering an organization’s security posture.
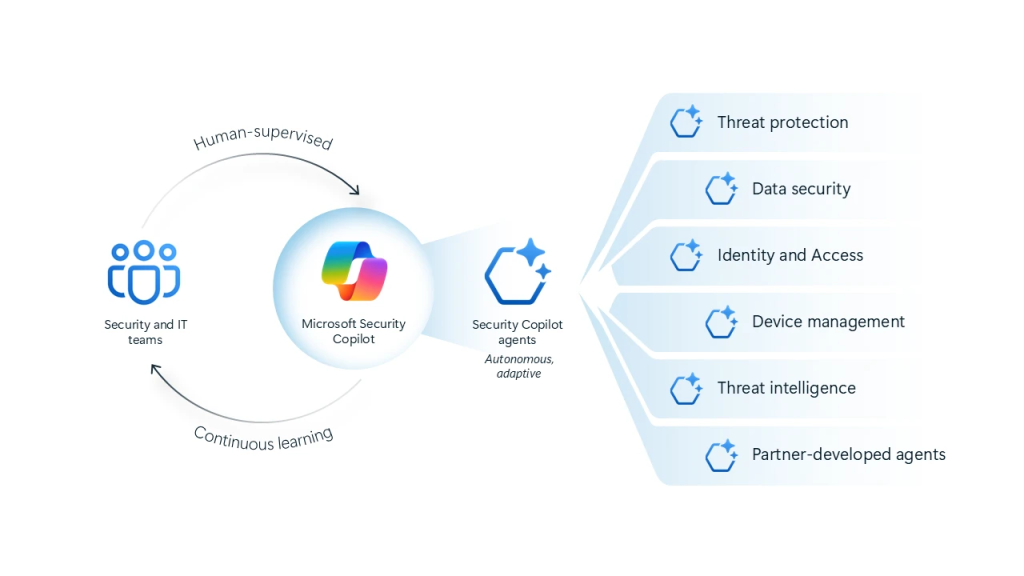
Security Copilot Agents are available across the Microsoft end-to-end security platform, designed for the following:
- Phishing Triage Agent in Microsoft Defender triages phishing alerts with accuracy to identify real cyberthreats and false alarms. It provides easy-to-understand explanations for its decisions and improves detection based on admin feedback.
- Alert Triage Agents in Microsoft Purview triage data loss prevention and insider risk alerts, prioritize critical incidents, and continuously improve accuracy based on admin feedback.
- Conditional Access Optimization Agent in Microsoft Entra monitors for new users or apps not covered by existing policies, identifies necessary updates to close security gaps, and recommends quick fixes for identity teams to apply with a single click.
- Vulnerability Remediation Agent in Microsoft Intune monitors and prioritizes vulnerabilities and remediation tasks to address app and policy configuration issues and expedites Windows OS patches with admin approval.
- Threat Intelligence Briefing Agent in Security Copilot automatically curates relevant and timely threat intelligence based on an organization’s unique attributes and cyberthreat exposure.
Conditional Access Optimization Agent in Microsoft Entra monitors for new users or apps not covered by existing policies, identifies necessary updates to close security gaps, and recommends quick fixes for identity teams to apply with a single click.
The Microsoft Entra Conditional Access Optimization Agent is a new AI-powered tool, currently in public preview, designed to help organizations enhance their CA policies by identifying gaps, recommending improvements, and consolidating redundant policies. It works in conjunction with Microsoft Security Copilot to provide intelligent, automated insights.
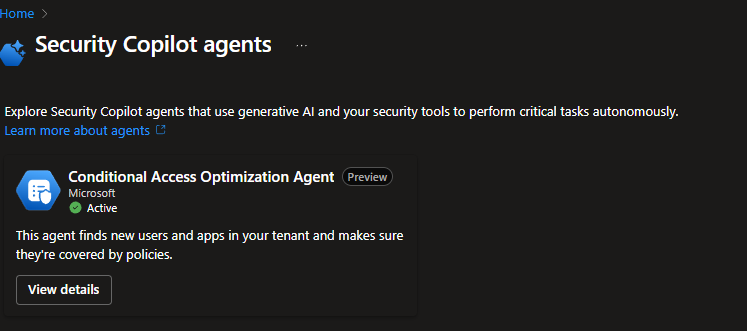
In plugin settings you can see Agent
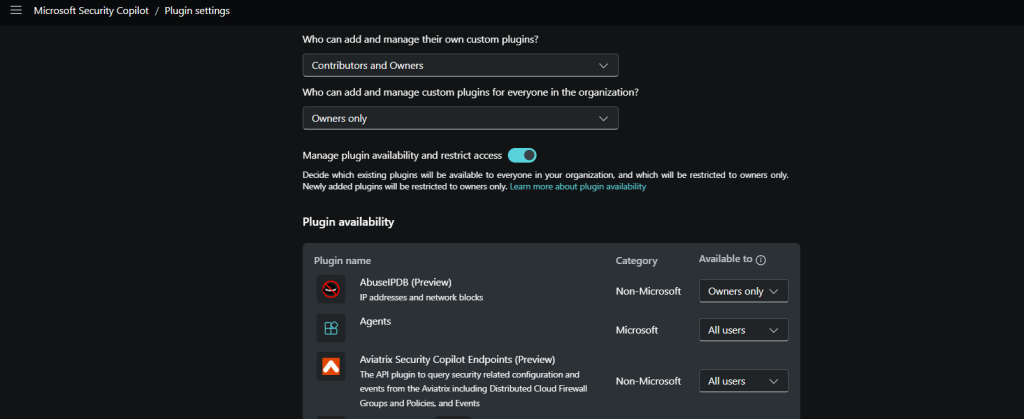
You must Allow Security Copilot to access data from your Microsoft 365 services
Go to https://securitycopilot.microsoft.com/ in order to create compute capacity
I tested Microsoft Entra Conditional Access optimization agent alongside Microsoft Security Copilot, utilizing 3 SCU.
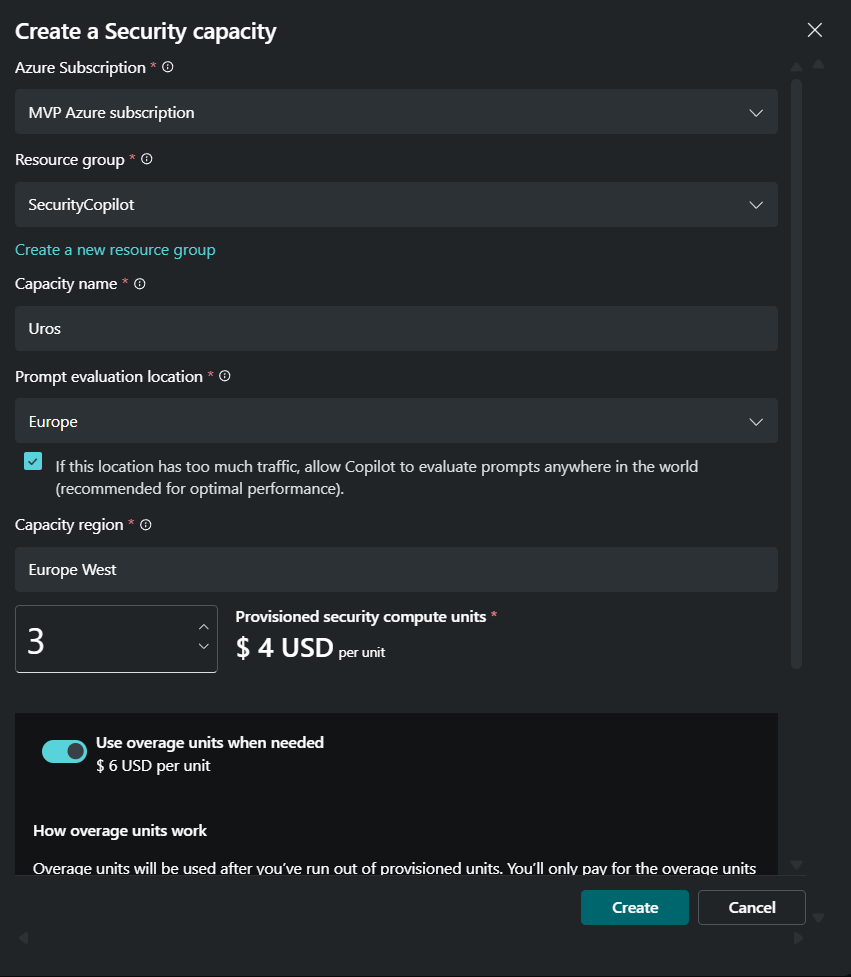
I also set max/limit 1 units per hour
Capacity created successfully
In Security Copilot Agent you can see Microsoft Entra Conditional Access optimization agent
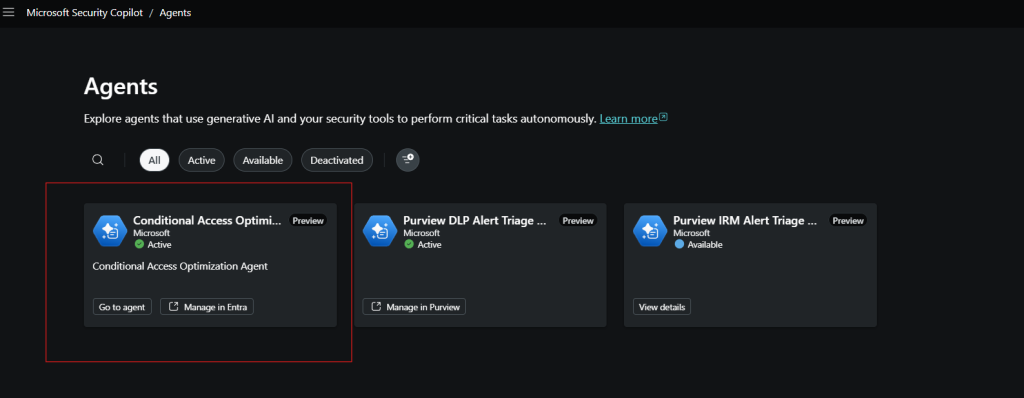
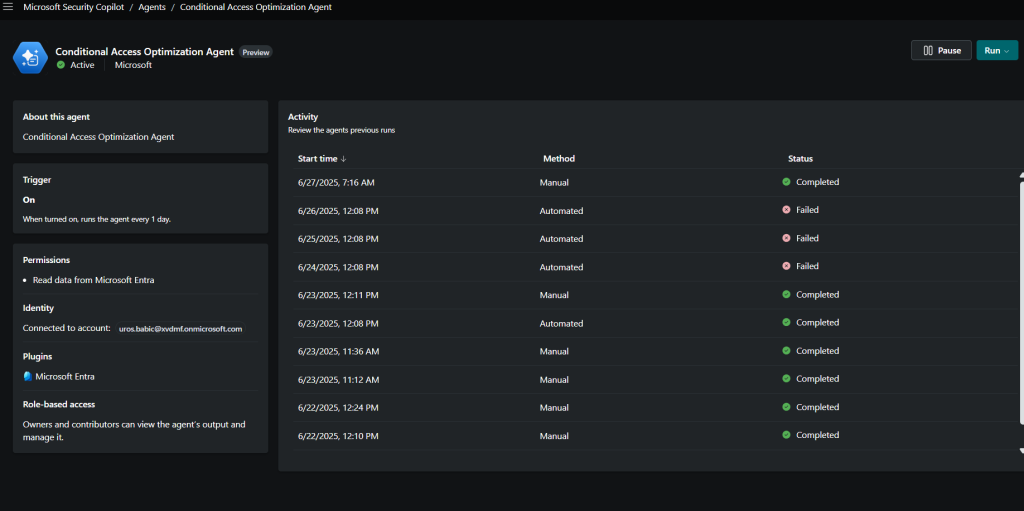
When I click agent can see Conditional Access Optimization Agent Dashboard with trigger ON
Permissions – Read data from Microsoft Entra
Connected to account: uros.babic@xvdmf.onmicrosoft.com
Plugins—Plugin Image—Microsoft Entra
Role-based access
Owners and contributors can view the agent’s output and manage it.
Activity- Review the agents previous runs
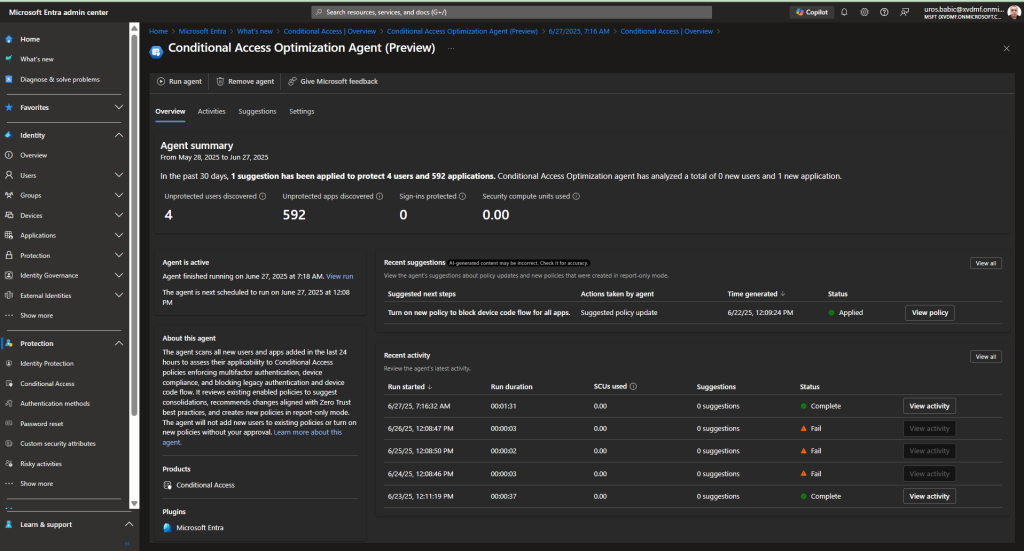
In https://entra.microsoft.com/ I can see Microsoft Entra Conditional Access optimization agent Dashboard
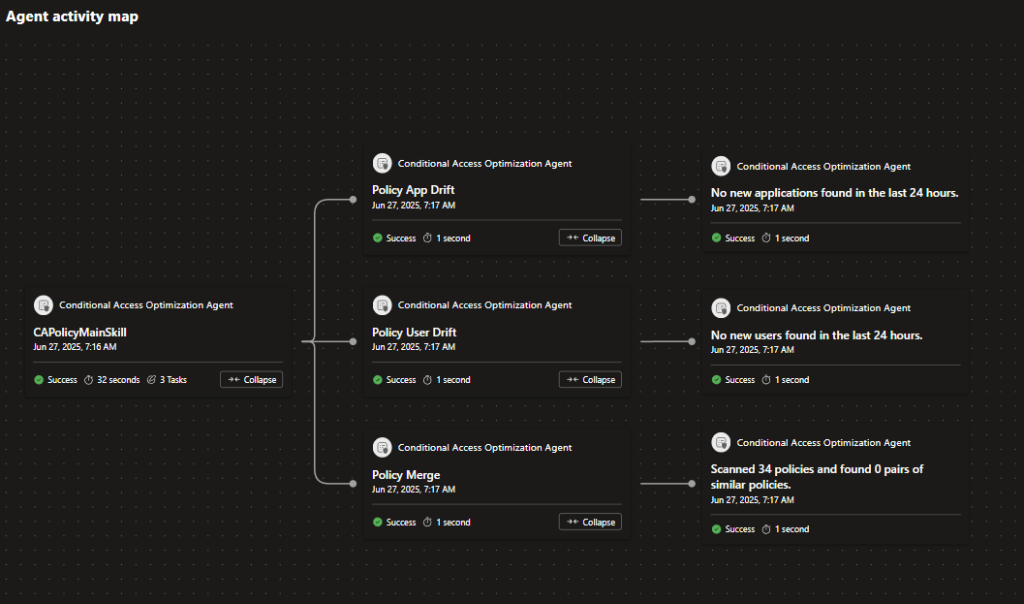
The agent activity map showcases great insights:
– Detection of CA policy user and application drift, implementation of policy merge
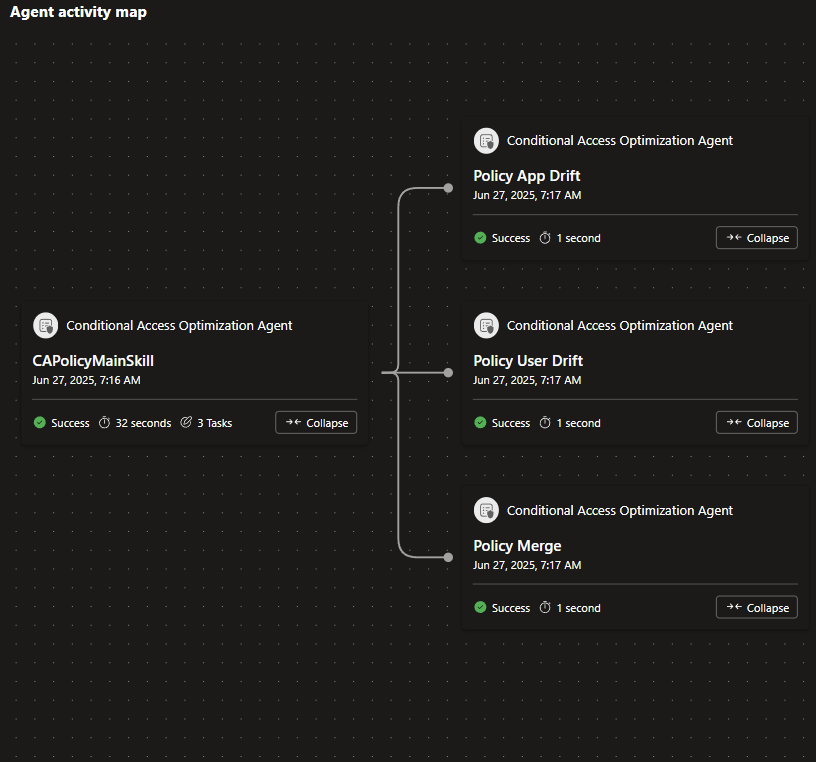
– Identification of new user activity within the last 24 hours
– Examination of scanned apps and recognition of new apps
– Review of scanned CA policy leading to the discovery of potentially similar policies
– Compilation of all new applications falling under the scope of at least one CAP
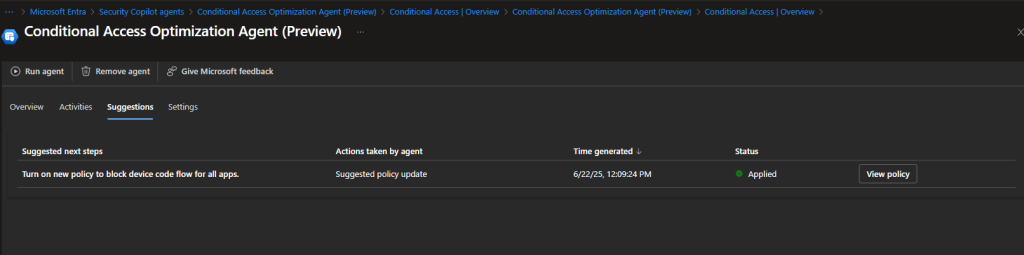
– Creation of a new reported-only CA policy named “Block device code flow”
– Exploration of new CA policy recommendations for updating existing CA policies
🔍Conditional Access optimization agent evaluates policies such as requiring MFA, enforcing device based controls (device compliance, app protection policies, and domain-joined devices), and blocking legacy authentication and device code flow, etc.
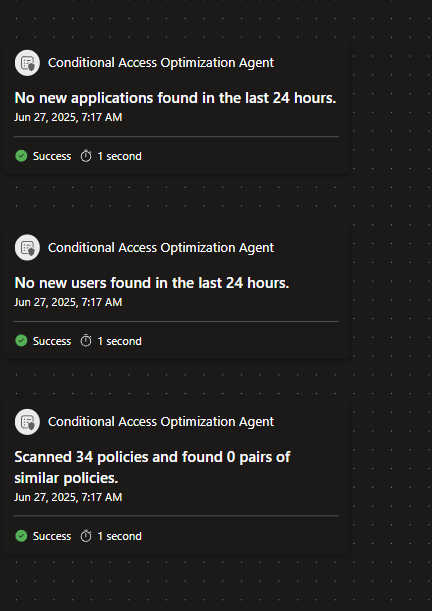
🔍The agent also found how many:
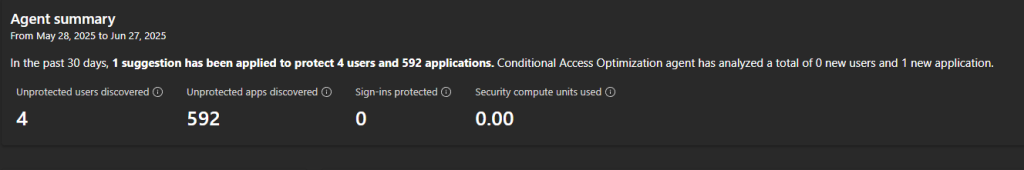
– new users unprotected.
-new applications unprotected.
– The agent also viewed all CA policies and found overlapping scopes that warranted consolidation at this time.
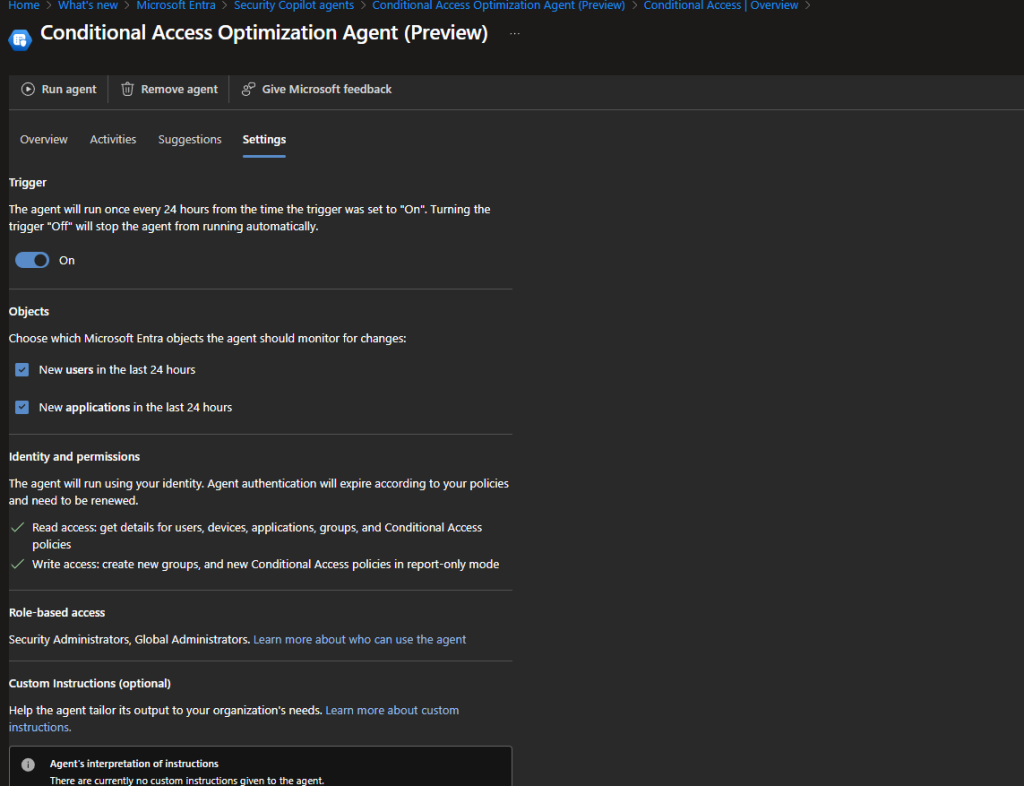
– The agent will run once every 24 hours from the time the trigger was set to “On”. Turning the trigger “Off” will stop the agent from running automatically.
Summary of agent activity
Conditional Access Optimization agent scanned the MSFT tenant starting on June 27, 2025 at 7:16:34 AM GMT+2. The agent completed run on June 27, 2025 at 7:17:06 AM GMT+2 and identified new users and new applications were added in the last 24 hours. The agent generated new policies in report-only mode and policy update suggestions based on Zero Trust best practices for your review.
The agent also reviewed all 34 existing CA policies and found no overlapping scopes that warranted consolidation at this time.
The agent found:
- new users unprotected.
- new applications unprotected.
Finally, you can see Agent activity map
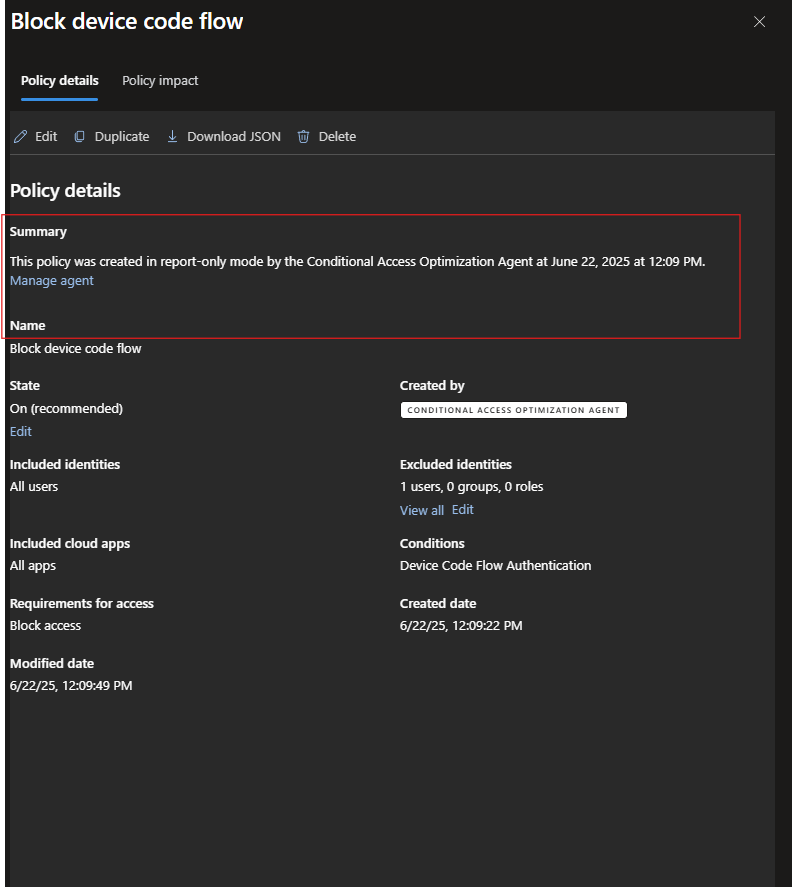
In Conditional access Policy, you can see Block device code flow
This policy was created in report-only mode by the Conditional Access Optimization Agent
Conditional Access optimization agent key features
The Conditional Access optimization agent scans your tenant for new users and applications and determines if Conditional Access policies are applicable.
In public preview, the key features include:
- Require MFA: The agent identifies users who aren’t covered by a Conditional Access policy that requires MFA and can update the policy.
- Require device-based controls: The agent can enforce device-based controls, such as device compliance, app protection policies, and domain-joined devices.
- Block legacy authentication: User accounts with legacy authentication are blocked from signing in.
- Policy consolidation: The agent scans your policy and identifies overlapping settings. For example, if you have more than one policy that has the same grant controls, the agent suggests consolidating those policies into one.
- Block device code flow: The agent looks for a policy blocking device code flow authentication.
- One-click remediation: When the agent identifies a suggestion, you can select Apply suggestion to have the agent update the associated policy with one click.
- Sign in to the Microsoft Entra admin center as at least a Security Administrator.
- From the new home page, select Go to agents from the agent notification card then select View details under the Conditional Access Optimization Agent.
Prerequisites and Limitations
Source Microsoft doc: https://learn.microsoft.com/en-us/entra/identity/conditional-access/agent-optimization
- You must have at least the Microsoft Entra ID P1 license.
- You must have available security compute units (SCU).
- On average, each agent run consumes less than one SCU.
- To activate the agent the first time, you need the Security Administrator or Global Administrator role during the preview.
- You can assign Conditional Access Administrators with Security Copilot access, which gives your Conditional Access Administrators the ability to use the agent as well.
- During the preview, avoid using an account to set up the agent that requires role activation with Privileged Identity Management (PIM). Using an account that doesn’t have standing permissions might cause authentication failures for the agent.
- Once agents are started, they can’t be stopped or paused. It might take a few minutes to run.
- For policy consolidation, each agent run only looks at four similar policy pairs.
- The agent currently runs as the user who enables it.
- In preview, you should only run the agent from the Microsoft Entra admin center.
- Scanning is limited to a 24 hour period.
- Suggestions from the agent can’t be customized or overridden.
The agent scans all new users and apps added in the last 24 hours to assess their applicability to Conditional Access policies enforcing multifactor authentication, device compliance, and blocking legacy authentication and device code flow. It reviews existing enabled policies to suggest consolidations, recommends changes aligned with Zero Trust best practices, and creates new policies in report-only mode. The agent will not add new users to existing policies or turn on new policies without your approval.
- Apply suggestion: The agent can apply the suggested changes to the policy with one click.
- Review policy changes: Review the policy changes before applying them.
- Policy impact: Displays a visualization of the potential impact of the policy
Policies in report-only mode that require a compliant device might prompt users on macOS, iOS, and Android devices to select a device certificate during policy evaluation, even though device compliance isn’t enforced. These prompts might repeat until the device is compliant. To prevent end users from receiving prompts during sign-in, exclude device platforms Mac, iOS, and Android from report-only policies that perform device compliance checks.
The agent is configured to run every 24 hours based on when it’s initially configured. You can run it at a specific time by toggling the Trigger setting off and then back on when you want it to run.
Suggested next steps
Suggested policy update
The agent runs under the identity and permissions of the user who enabled the agent in your tenant. Because of this requirement, you should avoid using an account that requires elevation like those that use PIM for just-in-time elevation.
The Security Administrator and Global Administrator roles also have access to Security Copilot by default
Remove agent
If you no longer wish to use the Conditional Access optimization agent, you can remove it using the Remove agent button at the top of the agent window.
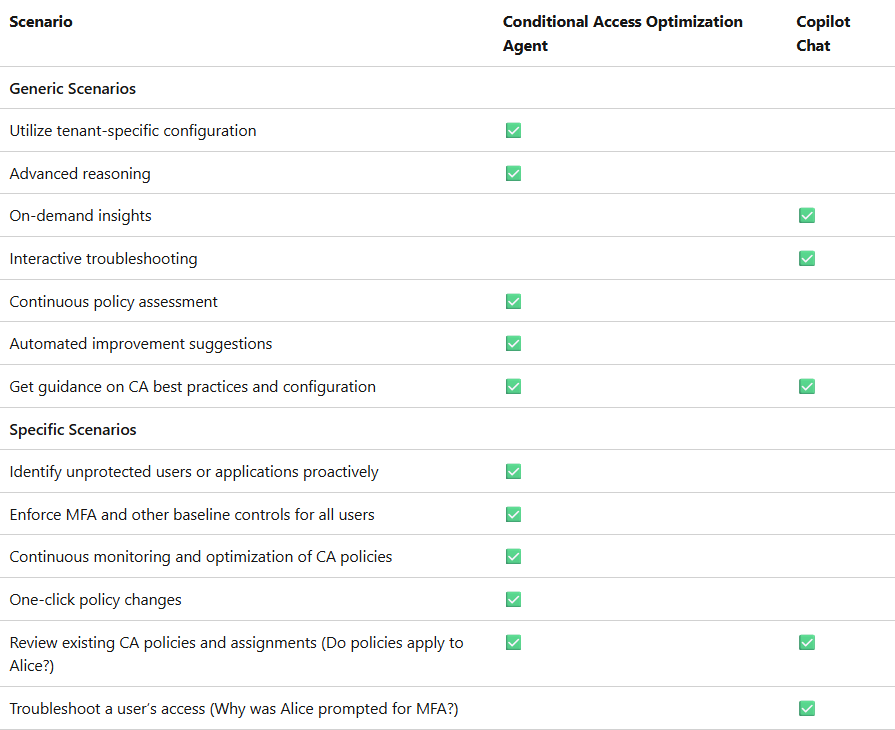
When should I use the Conditional Access optimization agent vs Copilot Chat?
Both features provide different insights into your Conditional Access policies. The following table provides a comparison of the two features:
In conclusion, the Conditional Access Optimization Agent in Microsoft Entra is a powerful AI-driven tool designed to help organizations enhance their security posture by:
- Identifying and addressing gaps in Conditional Access coverage
- Recommending and simplifying policies based on best practices
- Reducing complexity through policy consolidation
- Enabling safer enforcement with report-only mode and one-click remediation
It’s especially useful for organizations aiming to align with Zero Trust principles while maintaining operational efficiency.