GitHub Advanced Security (GHAS) plays a crucial role in enhancing the security posture of software development projects on GitHub. It provides a comprehensive set of tools and features designed to identify and address security vulnerabilities throughout the development lifecycle.
GitHub Advanced Security (or GHAS) is an application security solution that empowers developers. Advanced Security is embedded right into your workflow to help prevent vulnerabilities and credential leaks without slowing development. GitHub Advanced Security is like having your personal security consultant review every line of code with insights from security experts from around the world.
A GitHub Advanced Security license provides the following additional features for private repositories:
Code scanning – Search for potential security vulnerabilities and coding errors in your code using CodeQL or a third-party tool.
CodeQL CLI – Run CodeQL processes locally on software projects or to generate code scanning results for upload to GitHub.
CodeQL analysis consists of three steps:
- Preparing the code, by creating a CodeQL database.
- Running CodeQL queries against the database.
- Interpreting the query results.
Secret scanning – Detect secrets, for example keys and tokens, that have been checked into private repositories. If push protection is enabled, GitHub also detects secrets when they are pushed to your repository. Secret scanning alerts for users and push protection are available and free of charge for all public repositories on GitHub.com.
Custom auto-triage rules – Help you manage Dependabot alerts at scale. With custom auto-triage rules you have control over the alerts you want to ignore, snooze, or trigger a Dependabot security update for.
Dependency review – Show the full impact of changes to dependencies and see details of any vulnerable versions before you merge a pull request.
Using GitHub Advanced Security (GHAS) offers several benefits that can significantly enhance the security of your codebase and development workflow:
Proactive Vulnerability Detection: GHAS helps you identify and fix security vulnerabilities early in the development process through automated code scanning and dependency reviews.
Secret Protection: By scanning for secrets like API keys and tokens, GHAS prevents accidental exposure of sensitive information, reducing the risk of security breaches.
Comprehensive Security Insights: The Security Overview feature provides a centralized view of your security status across all repositories, making it easier to manage and prioritize security issues.
Automated Security Updates: GHAS can automatically generate pull requests to update vulnerable dependencies, ensuring your projects stay secure without manual intervention.
Compliance and Governance: GHAS helps organizations meet compliance requirements by providing detailed security reports and audit logs, which are essential for regulatory adherence.
Integration with Development Workflow: GHAS integrates seamlessly with GitHub’s development workflow, allowing developers to address security issues without leaving their familiar environment.
Enhanced Collaboration: Security alerts and insights can be shared with team members, fostering a collaborative approach to security and ensuring everyone is aware of potential risks
Code scanning

Code scanning is a feature that you use to analyze the code in a GitHub repository to find security vulnerabilities and coding errors. Any problems identified by the analysis are shown in your repository.
You can use code scanning to find, triage, and prioritize fixes for existing problems in your code. Code scanning also prevents developers from introducing new problems. You can schedule scans for specific days and times, or trigger scans when a specific event occurs in the repository, such as a push.
If code scanning finds a potential vulnerability or error in your code, GitHub displays an alert in the repository. After you fix the code that triggered the alert, GitHub closes the alert.
GitHub Copilot Autofix will suggest fixes for alerts from CodeQL analysis in private repositories, allowing developers to prevent and reduce vulnerabilities with less effort.
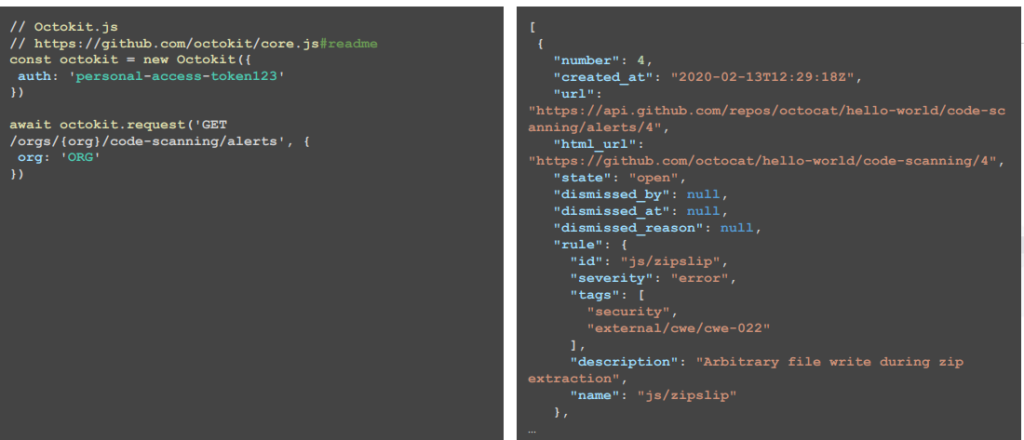
To monitor results from code scanning across your repositories or your organization, you can use webhooks and the code scanning API. For information about the webhooks for code scanning
Code scanning uses GitHub Actions, and each run of a code scanning workflow consumes minutes for GitHub Actions.
To use code scanning on a private repository, you will also need a license for GitHub Advanced Security.
You can configure code scanning to use the CodeQL product maintained by GitHub or a third-party code scanning tool.
CodeQL is the code analysis engine developed by GitHub to automate security checks. You can analyze your code using CodeQL and display the results as code scanning alerts.
Code scanning is interoperable with third-party code scanning tools that output Static Analysis Results Interchange Format (SARIF) data. SARIF is an open standard.
You can run third-party analysis tools within GitHub using actions or within an external CI system.
Secret scanning

Secret scanning is a crucial security feature within GitHub Advanced Security (GHAS) designed to identify and mitigate the inadvertent exposure of sensitive information, such as API keys and tokens within the source code.
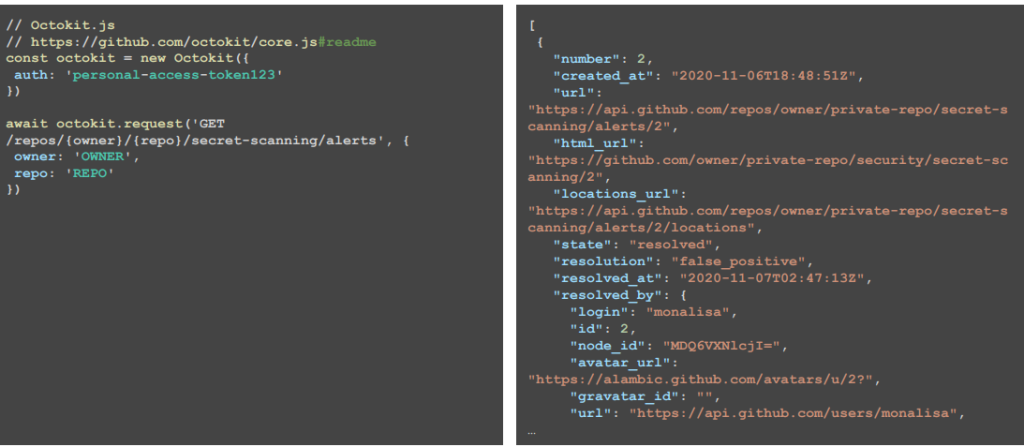
This scanning process is essential for preventing unauthorized access and safeguarding confidential data. Secret scanning operates by searching for predefined patterns and signatures indicative of sensitive information, ensuring that potential security risks are promptly addressed. By default, secret scanning looks for highly accurate patterns that have been provided by a GitHub Partner, however, custom patterns can be created for other use cases.
The following diagram summarizes the secret scanning process for public repositories, with any matches sent to a service provider’s verify endpoint.
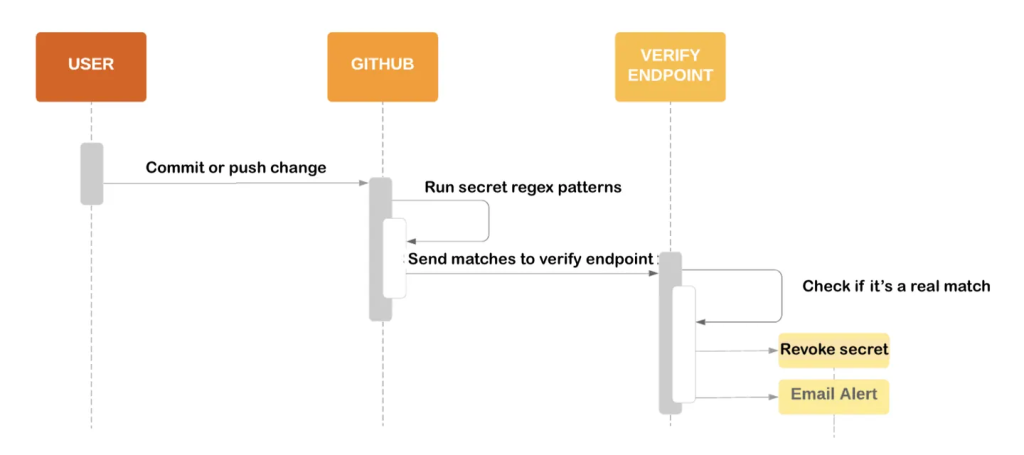
Secret scanning includes:
- Push protection proactively prevents secret leaks by scanning code on commit and blocking a push if a secret is present.
- The ability to easily view alerts and remediate them without ever having to leave GitHub.
In a secure software development life cycle, secret scanning plays a pivotal role in preventing unintentional leaks of critical information. By integrating secret scanning into the development process, teams can identify and remediate exposed secrets early, reducing the risk of data breaches and ensuring the confidentiality of sensitive data throughout the entire development life cycle.
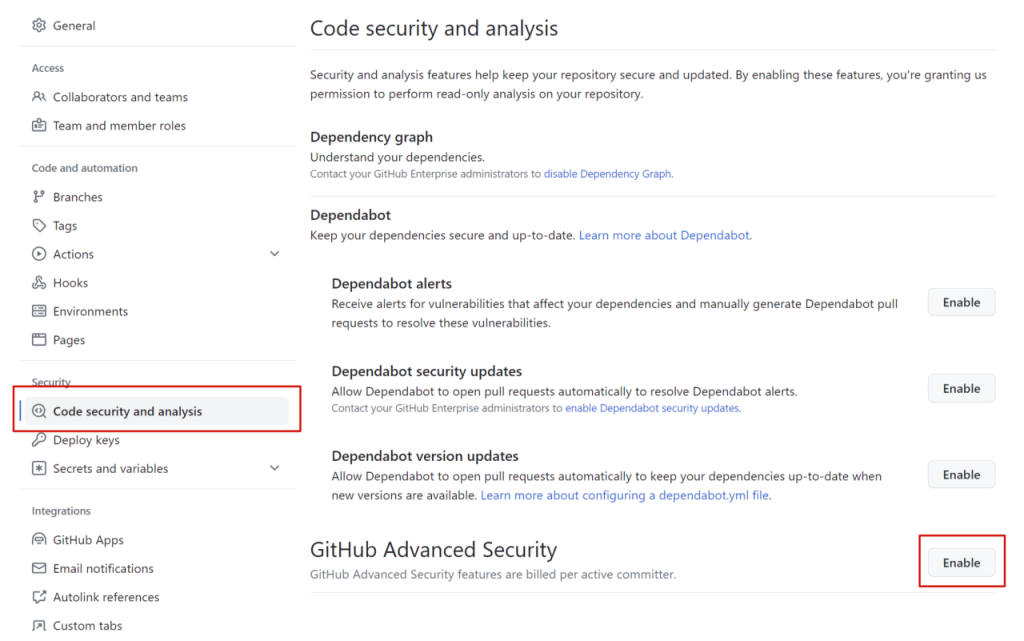
How Enable secret scanning?
Scroll down the page, and click Enable for secret scanning. If you see Disable, that means that secret scanning is already enabled for the repository.
Dependabot

Dependabot is an automated dependency management tool, responsible for keeping project dependencies up-to-date. It regularly checks for updates to libraries and frameworks used in a project and automatically opens pull requests to update dependencies to their latest, secure versions. Dependabot contributes to maintaining a secure and stable development environment by addressing vulnerabilities present in outdated dependencies.
In a secure software development life cycle, managing dependencies is crucial to minimizing the risk of exploiting known vulnerabilities. Dependabot streamlines the process of updating dependencies, ensuring that projects benefit from the latest security patches and improvements. By automating this aspect of security, Dependabot contributes to creating a resilient and secure foundation for the entire development process.
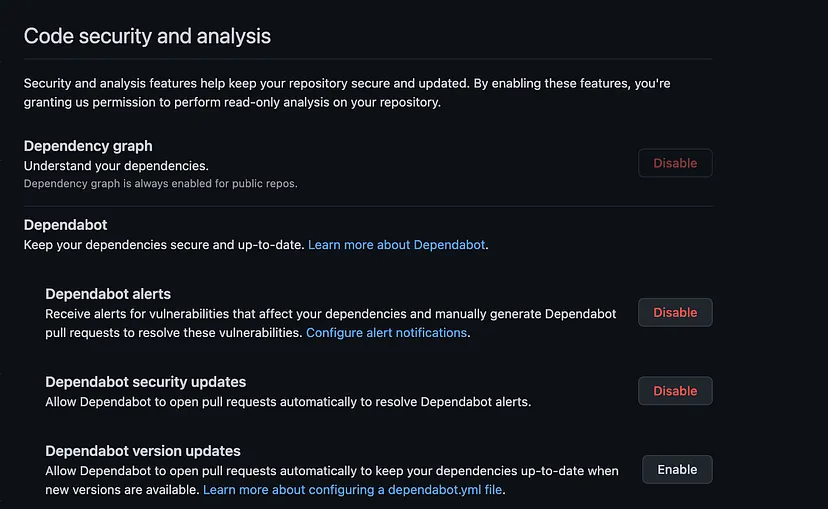
With GitHub Advanced Security, Dependabot’s functionality is extended to include Dependency Review, allowing you to check for vulnerable dependencies within a pull request. This check enables you to address vulnerabilities before they are merged into a shared branch.
To enable any of the alerts from a repository level first navigate to your repository’s security tab.
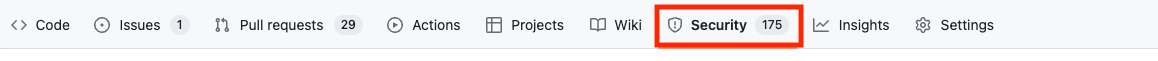
Next, enable your alerts in the Security overview.
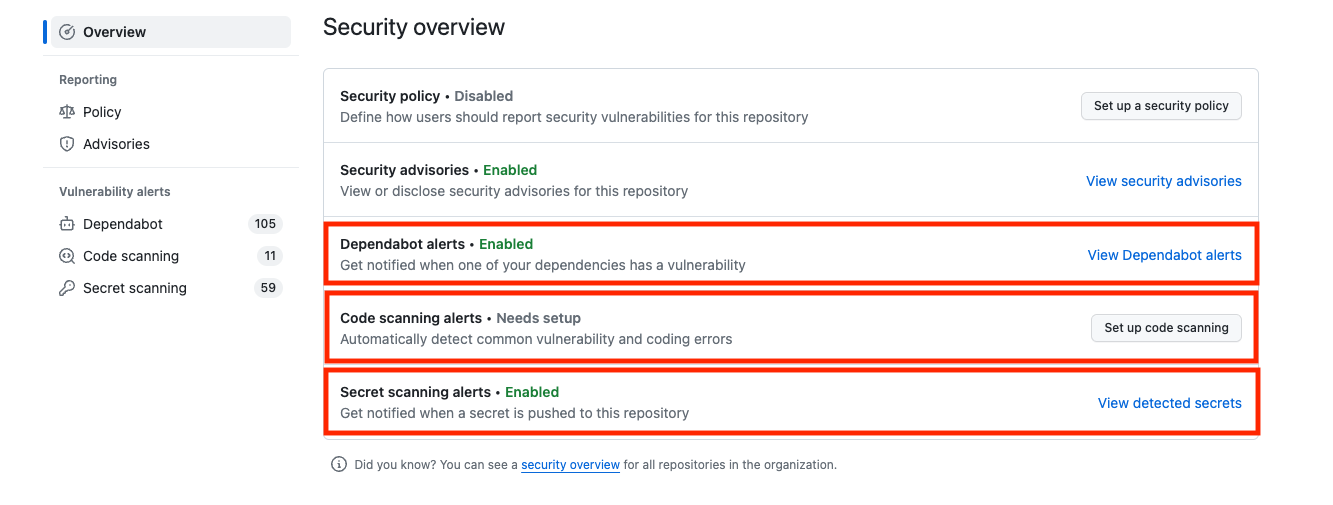
Secret scanning, code scanning, and Dependabot collectively contribute to creating a more secure software development life cycle. Secret scanning prevents inadvertent exposure of sensitive information. Code scanning identifies and addresses security vulnerabilities in the codebase. And Dependabot automates dependency management.
By integrating these features, development teams can proactively address security concerns at every stage of the development life cycle. This proactive approach minimizes the likelihood of security incidents reaching production, resulting in a more resilient, secure, and efficient software development process.
The combined impact of these integral features ensures that security is not a standalone consideration but an integral part of the entire development workflow.
Security features for open source projects
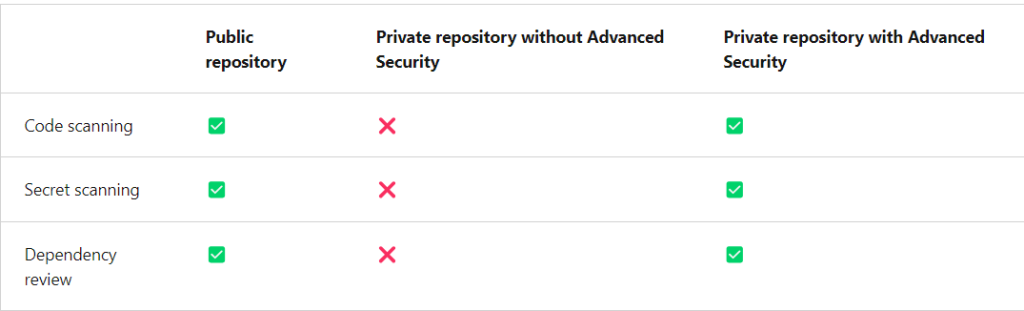
Public projects on GitHub benefit from certain default security features, such as secret scanning and dependency graphs. GitHub automatically scans public repositories for partner patterns and provides alerts to repository administrators. Public projects can also choose to enable code scanning, Dependabot, and Dependency Review without a GitHub Advanced Security license.
However, these features are foundational and may not provide the depth of protection needed for more complex projects or enterprise environments.
When GitHub Advanced Security (GHAS) is paired with GitHub Enterprise Cloud (GHEC), the comprehensive set of security features becomes available for internal and private projects as well:
- Code scanning – Search for potential security vulnerabilities and coding errors in your code.
- Secret scanning – Detect secrets, for example, keys and tokens, that have been checked into private repositories. Secret scanning alerts for users and partners are available and free of charge for public repositories on GitHub.com. If push protection is enabled, it also detects secrets when they are pushed to your repository.
- Dependency review – Show the full impact of changes to dependencies and see details of any vulnerable versions before you merge a pull request. The table below summarizes the availability of GitHub Advanced Security features for public and private repositories.
To generate the dependency graph, GitHub looks at a repository’s explicit dependencies declared in the manifest and lockfiles. When enabled, the dependency graph automatically parses all known package manifest files in the repository and uses this scan to construct a graph with known dependency names and versions.
Key points about the dependency graph include:
- Includes information on your direct dependencies and transitive dependencies.
- Dependency graph is automatically updated when you push a commit to GitHub that changes or adds a supported manifest or lock file to the default branch. It’s also automatically updated when anyone pushes a change to the repository of one of your dependencies as well.
- You can see the dependency graph by opening the repository’s main page on GitHub and navigating to the Insights tab.
- If you have at least read access to the repository, you can export the dependency graph for the repository as an SPDX-compatible, Software Bill of Materials (SBOM), via the GitHub UI or GitHub REST API.
Other supply chain features on GitHub rely on the information provided by the dependency graph, which include the following:
- Dependency review: uses the dependency graph to identify dependency changes and help you understand the security impact of these changes when you review pull requests.
- Dependabot alerts: Dependabot cross-references dependency data provided by the dependency graph with the list of advisories published in the GitHub Advisory Database. The dependency graph scans your dependencies and generates Dependabot alerts when a potential vulnerability is detected.
- Dependabot security updates: Uses the dependency graph and Dependabot alerts to help you update dependencies with known vulnerabilities in your repository.
Acting on GHAS alerts
GitHub Advanced Security (GHAS) provides a suite of tools to help you build more secure code. When it comes to acting on GHAS alerts, here are some key steps you can follow:
- Understand the Alerts: GHAS generates alerts for various security issues, including vulnerabilities in your code and exposed secrets. Familiarize yourself with the types of alerts you might receive.
- Prioritize Alerts: Not all alerts are of equal importance. Prioritize them based on the severity and potential impact on your project. Critical vulnerabilities should be addressed first.
- Investigate and Fix: For each alert, investigate the root cause. Use the information provided by GHAS to understand the issue and apply the necessary fixes. This might involve updating dependencies, refactoring code, or changing configurations.
- Document and Communicate: Keep a record of the alerts and the actions taken to resolve them. Communicate with your team about the issues and the fixes applied to ensure everyone is aware and can learn from them.
- Automate Where Possible: Use automation tools to handle repetitive tasks. For example, you can set up automated workflows to scan for vulnerabilities regularly and notify the relevant team members.
- Review and Improve: Regularly review the alerts and the actions taken. Look for patterns and areas where you can improve your codebase and security practices to prevent similar issues in the future.
Code Scanning Alerts:
- CodeQL Analysis Alerts: Generated by CodeQL, GitHub’s semantic code analysis engine, these alerts identify potential security vulnerabilities in the codebase. They cover a wide range of issues, including but not limited to SQL injection, cross-site scripting, and other code vulnerabilities.
Secret Scanning Alerts:
- Exposed Secrets Alerts: These alerts are triggered when potentially sensitive information, such as API keys or credentials, is identified within the repository’s source code. Secret scanning helps prevent accidental exposure of confidential data.
Dependency Alerts:
- Dependabot Alerts: Dependabot automatically detects outdated dependencies in a project and creates pull requests to update them to the latest, secure versions. Dependabot alerts notify developers about available updates for project dependencies.
Security Overview Alerts:
- The Security Overview provides a comprehensive dashboard summarizing the security status of the repository.
Third Party Alerts:
- You can integrate third-party code analysis tools with GitHub code scanning by uploading data as SARIF files.
GHAS provides granular access controls, allowing organizations to define who can view alerts for different security features. This ensures that only authorized personnel, such as security teams and relevant stakeholders, have access to sensitive security information.
Access management is role-based, with different roles having varying levels of access to GHAS alerts:
- Code scanning & Dependabot alerts can be seen and modified by anyone with the
Writerepository role - Secret scanning alerts can be seen and modified by anyone with the
Adminrepository role - Any person or team can be granted access to see and modify all alerts on a repository, regardless of their repository role, by modifying the repo’s “Access to alerts” settings
Understand GHAS and its role in the security ecosystem
This approach ensures that security considerations are addressed from the project’s inception, resulting in faster identification and resolution of vulnerabilities.
- Early Detection: Integrating security early allows for the detection of vulnerabilities at the source code level, minimizing the likelihood of issues reaching production.
- Efficient Remediation: Security issues can be addressed promptly as part of regular development activities, reducing the time and effort required to understand the context of the issue.
- Consistent Security Standards: Integration ensures consistent adherence to security standards across the entire development life cycle, fostering a proactive security culture within the development team.
- Improved Collaboration: Collaboration between developers, security teams, and other stakeholders is enhanced, as security becomes a shared responsibility throughout the development process.
By understanding and implementing these advanced security practices with the help of GHAS, organizations can significantly enhance their software development processes and create a more resilient and secure development ecosystem.
GHAS empowers DevSecOps teams to prioritize innovation and enhance developer productivity without sacrificing security. Automated security checks are run with every pull request, surfacing issues in the context of the development workflow so vulnerabilities are fixed in minutes, not months.
About GitHub Advanced Security Certification

- The exam is 120 minutes long.
- The exam consists of around 73 multiple-choice questions, of which only 60 are scored and contribute to your final score.
- The exam can be taken online (proctored, available through PSI) or in person (available at select testing centers).
- An official passing score is not provided.
- You can reschedule or cancel your exam up to 48 hours before your scheduled exam time.
- If you fail the exam, you must wait 24 hours before attempting the first retake. After that, you must wait 14 days between each consecutive retake. There is a limit of 5 total attempts.
Passing the exam will grant you the GitHub Advanced Security certification, and a badge and a certificate from Credly. The certification is valid for 3 years.
Conclusion
In summary, GitHub Advanced Security (GHAS) offers a robust set of tools to enhance the security of your codebase. By enabling features like code scanning, secret scanning, and dependency review, you can proactively identify and mitigate vulnerabilities, protect sensitive information, and maintain compliance with security standards. Integrating these tools into your development workflow ensures that security is a continuous and collaborative effort.