- Microsoft Defender for Cloud Apps overview
Microsoft Defender for Cloud Apps delivers full protection for SaaS applications, helping you monitor and protect your cloud app data across the following feature areas:
- Fundamental cloud access security broker (CASB) functionality, such as Shadow IT discovery, visibility into cloud app usage, protection against app-based threats from anywhere in the cloud, and information protection and compliance assessments.
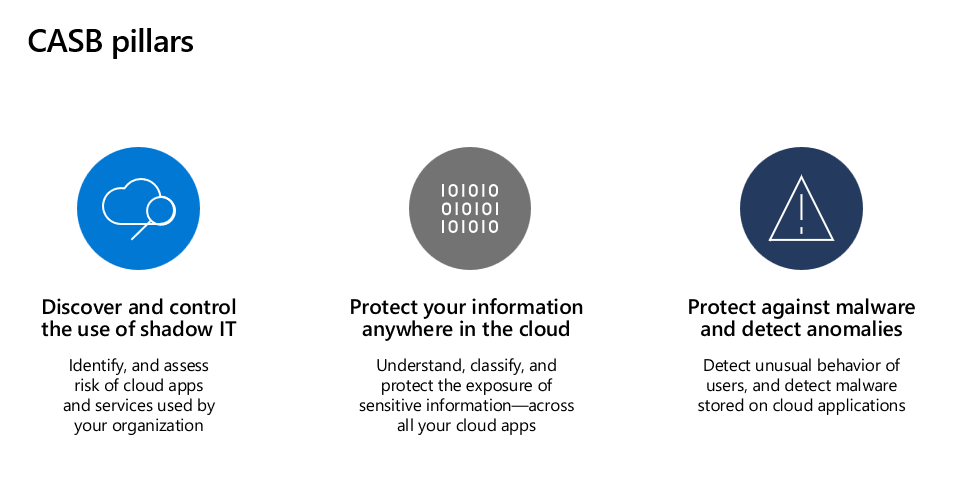
- SaaS Security Posture Management (SSPM) features, enabling security teams to improve the organization’s security posture
- Advanced threat protection, as part of Microsoft’s extended detection and response (XDR) solution, enabling powerful correlation of signal and visibility across the full kill chain of advanced attacks
- App-to-app protection, extending the core threat scenarios to OAuth-enabled apps that have permissions and privileges to critical data and resources.
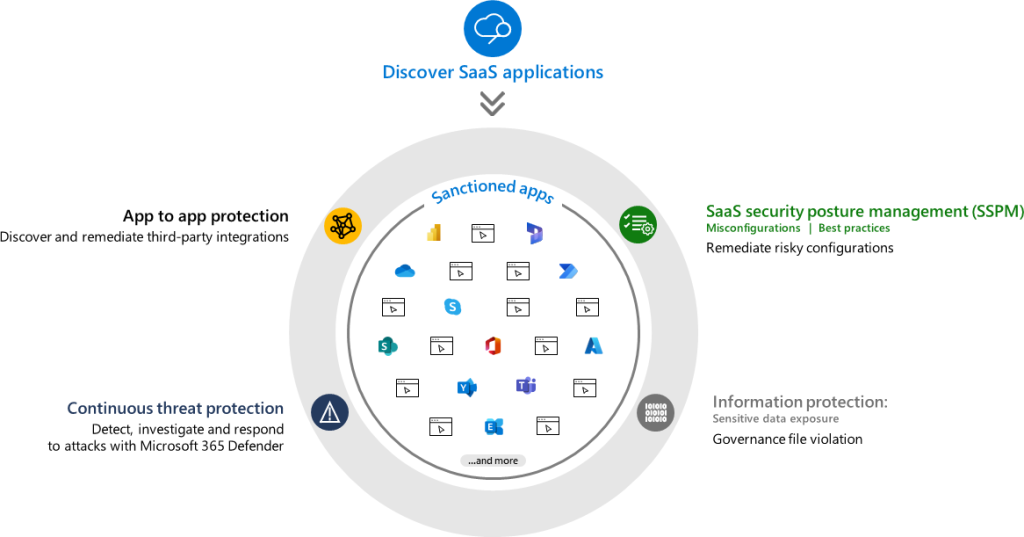
Microsoft Defender for Cloud apps is a primary component of a Zero Trust strategy as a part Zero Trust architecture and XDR deployment with Microsoft Defender XDR. Microsoft Defender for Cloud Apps gathers signals from organization’s use of cloud apps and protects data flowing between your environment and these apps, including both sanctioned and unsanctioned cloud apps.
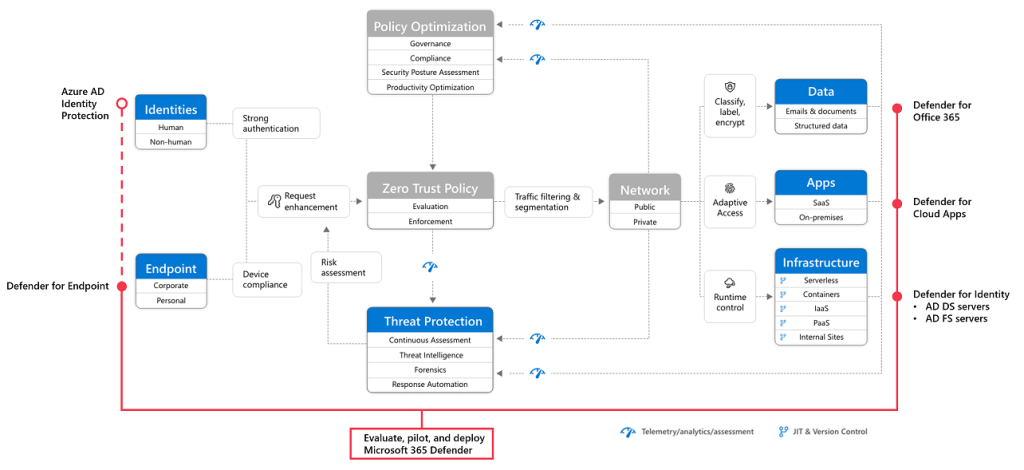
Respond to threats with Defender for Cloud Apps’s user and entity behavioral analytics (UEBA) and anomaly detection, malware protection, OAuth app protection, incident investigation, and remediation. Monitor for security anomaly alerts, such as for impossible travel, suspicious inbox rules, and ransomware. Focus on identifying app usage patterns, assessing risk levels and business readiness of apps, preventing data leaks to noncompliant apps, and limiting access to regulated data.
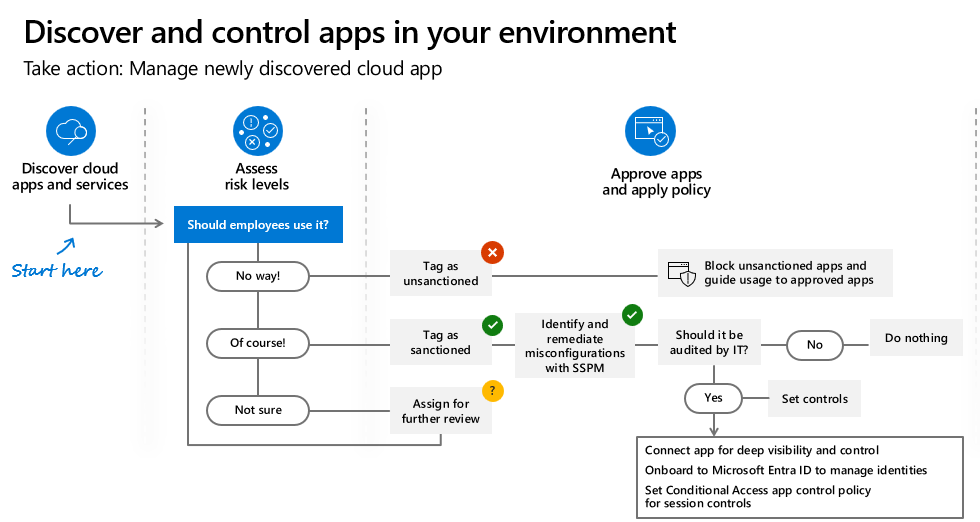
Organizations can’t apply access policies to apps they don’t know are being used. Discovery of the cloud apps and services being used in your organization allows you to assess those cloud resources for risk and decide whether to approve and apply policy or block and guide usage towards other approved apps and resources.
2. Cloud discovery and security posture management
2.1. Cloud app discovery overview
Cloud discovery analyzes traffic logs against the Microsoft Defender for Cloud Apps catalog of over 31,000 cloud apps. The apps are ranked and scored based on more than 90 risk factors to provide you with ongoing visibility into cloud use, Shadow IT, and the risk Shadow IT poses into your organization
You can generate the following types of reports:
- Snapshot reports – Provides ad-hoc visibility on a set on traffic logs you manually upload from your firewalls and proxies.
- Continuous reports – Analyze all logs that are forwarded from your network using Defender for Cloud Apps. They provide improved visibility over all data, and automatically identify anomalous use using either the Machine Learning anomaly detection engine or by using custom policies that you define. These reports can be created by connecting in the following ways:
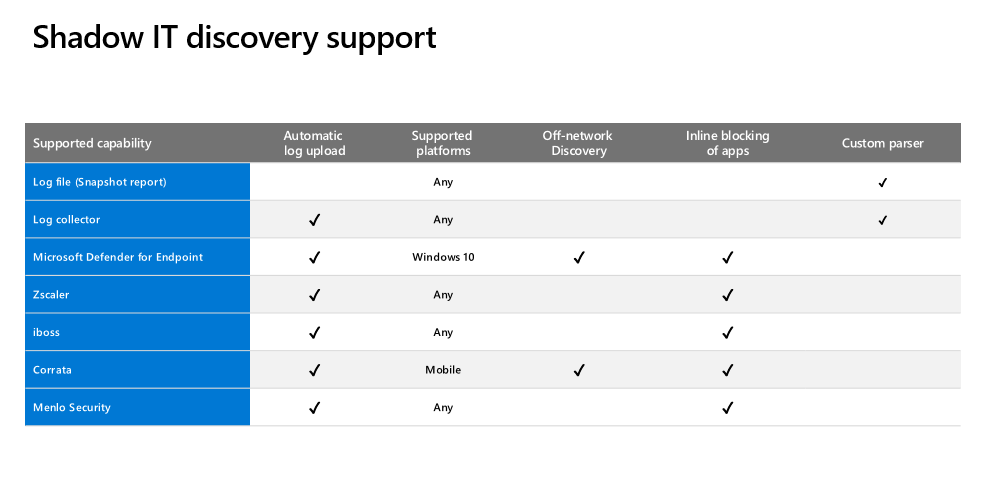
- Microsoft Defender for Endpoint integration: Defender for Cloud Apps integrates with Defender for Endpoint natively, to simplify rollout of cloud discovery, extend cloud discovery capabilities beyond your corporate network, and enable machine-based investigation.
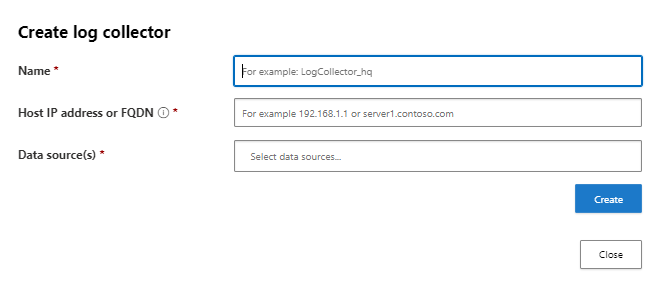
- Log collector: Log collectors enable you to easily automate log upload from your network. The log collector runs on your network and receives logs over Syslog or FTP.
- Secure Web Gateway (SWG): If you work with both Defender for Cloud Apps and one of the following SWGs, you can integrate the products to enhance your security cloud discovery experience. Togethers Defender for Cloud Apps and SWGs provide seamless deployment of cloud discovery, automatic blocking of unsanctioned apps, and risk assessment directly in the SWG’s portal.
- Cloud discovery API – Use the Defender for Cloud Apps cloud discovery API to automate traffic log upload and get automated cloud discovery report and risk assessment. You can also use the API to generate block scripts and streamline app controls directly to network appliance.
Log process flow generating a risk assessment consists of the following steps:
- Upload – Web traffic logs from your network are uploaded to the portal.
- Parse – Defender for Cloud Apps parses and extracts traffic data from the traffic logs with a dedicated parser for each data source.
- Analyze – Traffic data is analyzed against the cloud app catalog to identify more than 31,000 cloud apps and to assess their risk score. Active users and IP addresses are also identified as part of the analysis.
- Generate report – A risk assessment report of the data extracted from log files is generated.
2.3. How to create snapshot cloud discovery reports
It’s important to upload a log manually and let Microsoft Defender for Cloud Apps parse it before trying to use the automatic log collector.
To create a snapshot report:
Collect log files from your firewall and proxy, through which users in your organization access the Internet. Make sure to gather logs during times of peak traffic that are representative of all user activity in your organization.
In the Microsoft Defender Portal, under Cloud Apps, select Cloud discovery.
In the top-right corner, pull down Actions, and select Create Cloud Discovery snapshot report.
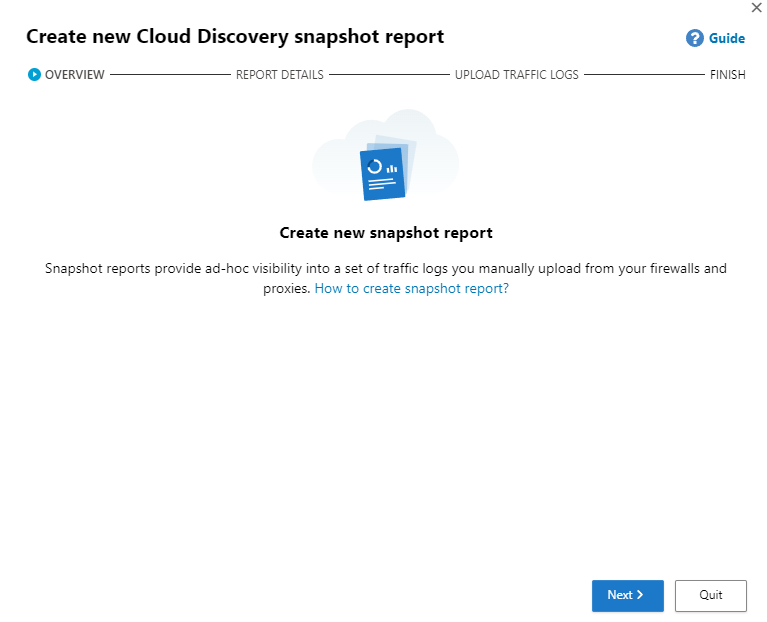
Select Next and Enter a Report name , Description and Source
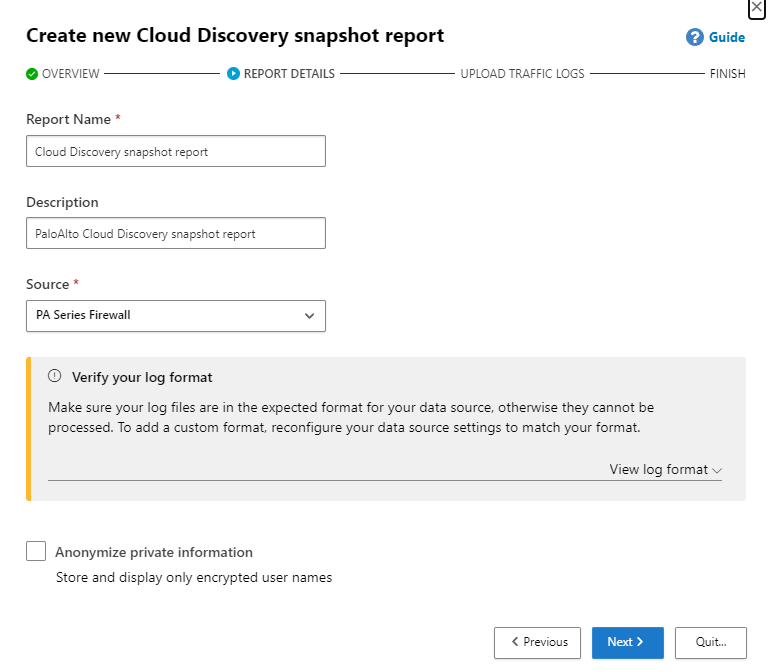
Snapshot report provide visibility into cloud app activity and use traffic logs that you upload
Cloud discovery uses the data in traffic logs. Cloud discovery requires web-traffic data with the following attributes:
- Date of the transaction
- Source IP
- Source user – highly recommended
- Destination IP address
- Destination URL recommended (URLs provide higher accuracy for cloud app detection than IP addresses)
- Total amount of data (data information is highly valuable)
- Amount of uploaded or downloaded data (provides insights about the usage patterns of the cloud apps)
- Action taken (allowed/blocked)
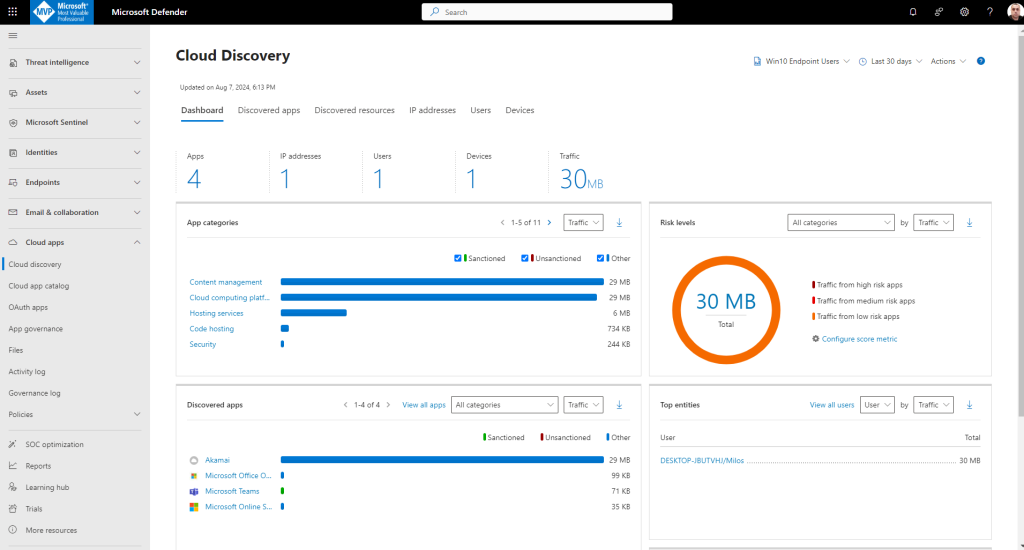
Finally you can see Cloud discovery report with all necessary information about apps, ip address, users, devices, traffic, App categories, Risk levels, Discovered apps, top entities by users, etc.
2.4 How to calculate risk score
The Microsoft Defender for Cloud Apps Cloud app catalog page provides a full list of over 31,000 discoverable cloud apps. Defender for Cloud Apps discovery analyzes your traffic logs against discoverable cloud apps to give you ongoing visibility into cloud use, Shadow IT, and risks posed to your organization. Use the Cloud apps catalog to identify the apps that fit into your organization’s security requirements.
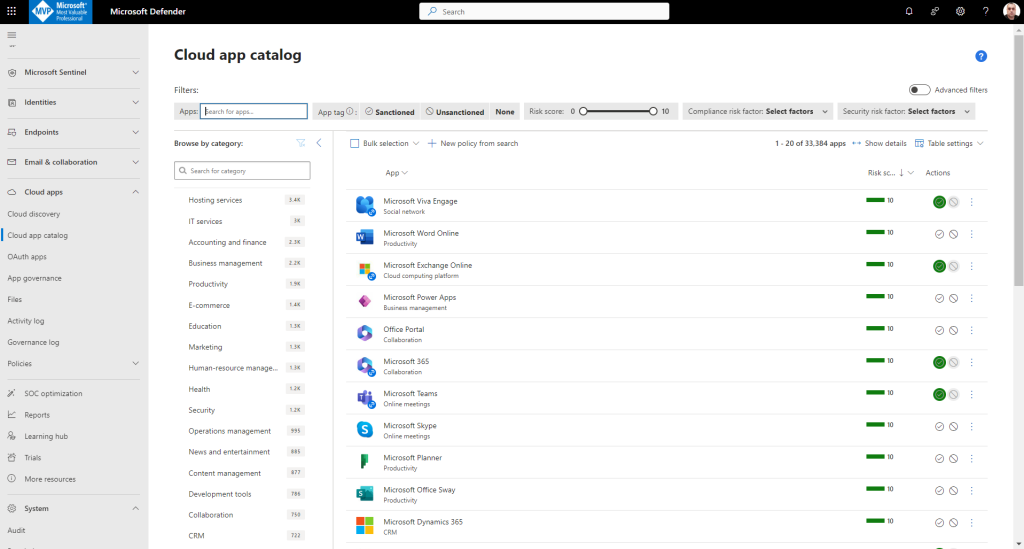
Apps in the cloud app catalog are scored based on more than 90 risk factors.
Defender for Cloud Apps rates risks based on regulatory certification, industry standards, and best practices. The score represents the Defender for Cloud Apps assessment of this particular app’s maturity of use for enterprises.
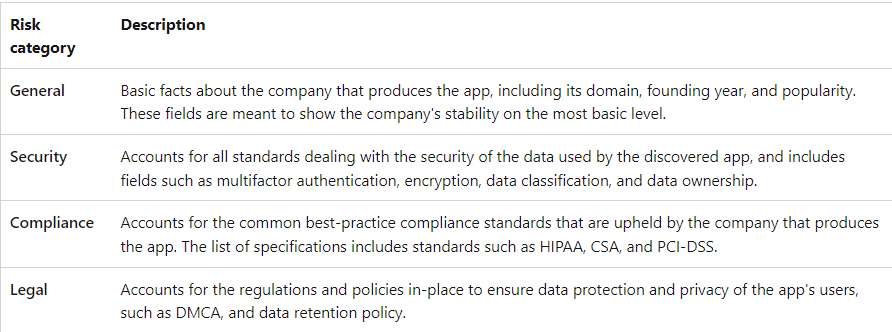
Risk scores are kept up to date using the following sources:
Data automatically extracted from the cloud app, for attributes such as SOC 2 compliance, terms of service, sign-in URL, privacy policy, and HQ location.
Data automatically extracted using advanced Defender for Cloud App algorithms, for attributes such as HTTP security headers.
Continuous analysis by the Defender for Cloud Apps analysis team, for attributes such as encryption at rest.
Customer requests for changes to the cloud app catalog
You can customize the risk score sign into Microsoft Defender XDR and select Settings > Cloud Apps > Cloud Discovery > Score metrics.
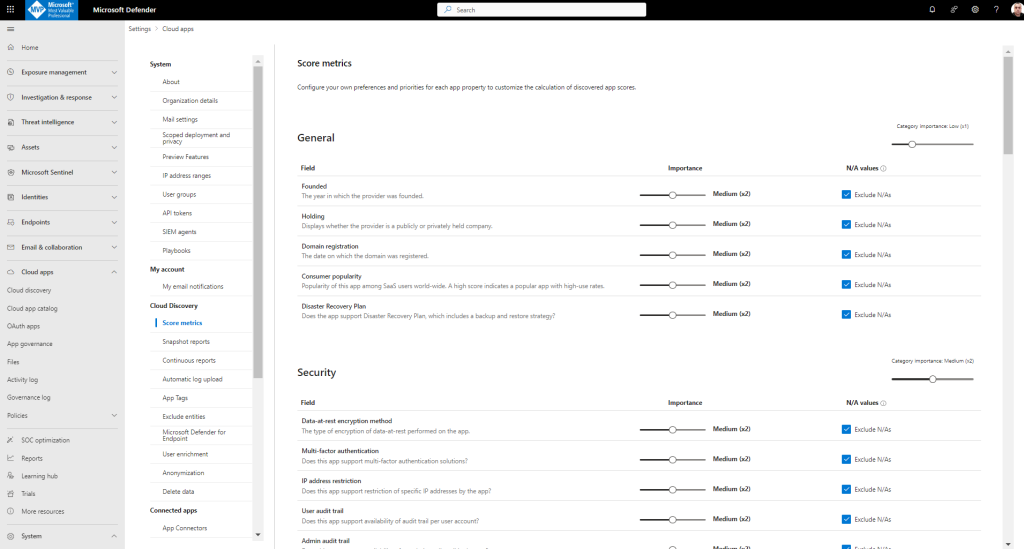
For each field or risk category slide the Importance slide to change the weight of the field or the risk category. Importance can be set to Ignored, Low, Medium, High, or Very High.
2.5 Connect apps to get visibility and control
Microsoft Defender for Cloud Apps leverages the APIs provided by the cloud provider. All communication between Defender for Cloud Apps and connected apps is encrypted using HTTPS. Each service has its own framework and API limitations such as throttling, API limits, dynamic time-shifting API windows, and others. Microsoft Defender for Cloud Apps worked with the services to optimize the usage of the APIs and to provide the best performance.
Defender for Cloud Apps supports multiple instances of the same connected app. For example, if you have more than one instance of Salesforce (one for sales, one for marketing) you can connect both to Defender for Cloud Apps. You can manage the different instances from the same console to create granular policies and deeper investigation. This support applies only to API connected apps, not to Cloud Discovered apps or Proxy connected apps.
The App Connector flow is as follows:
Defender for Cloud Apps scans and saves authentication permissions.
Defender for Cloud Apps requests the user list. The first time the request is done, it may take some time until the scan completes. After the user scan is over, Defender for Cloud Apps moves on to activities and files. As soon as the scan starts, some activities will be available in Defender for Cloud Apps.
After completion of the user request, Defender for Cloud Apps periodically scans users, groups, activities, and files. All activities will be available after the first full scan.
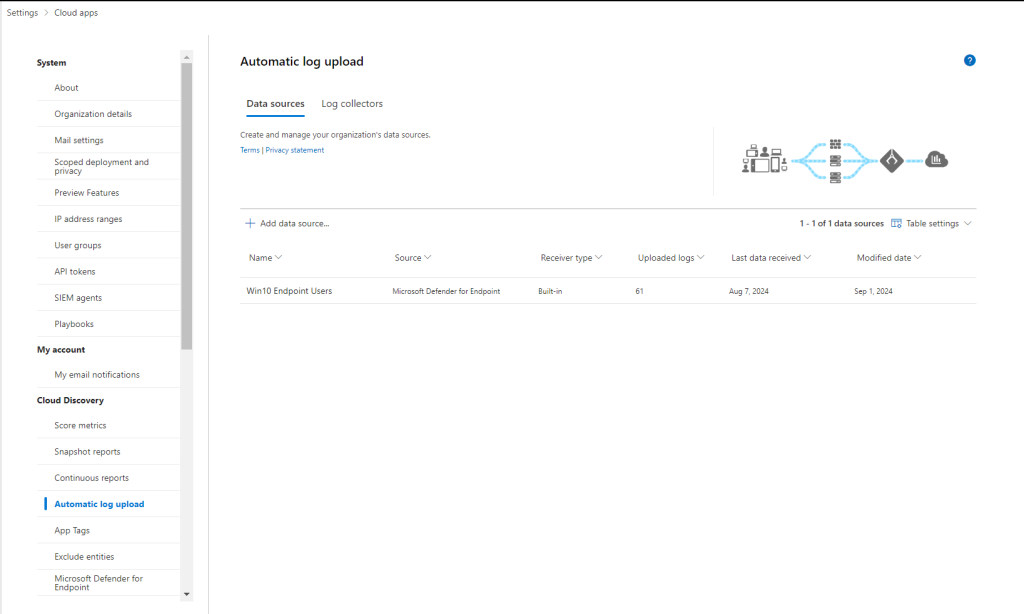
2.6. Configure automatic log upload for continuous reports
You can upload traffic logs with activities up to 90 days old and up to 1GB in size per log file
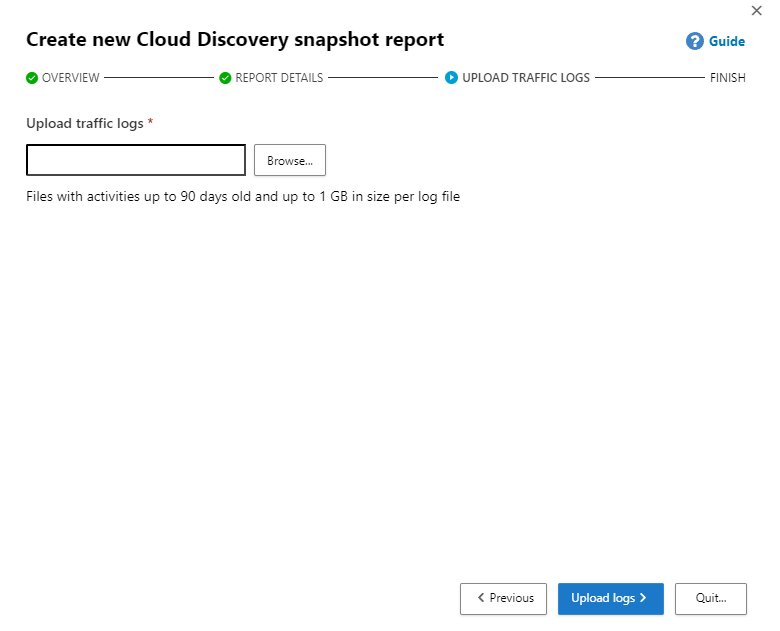
Select Upload logs. After upload completes, the status message will appear at the top-right corner of your screen letting you know that your log was successfully uploaded.
After you upload your log files, it will take some time for them to be parsed and analyzed. After processing of your log files completes, you’ll receive an email to notify you that it’s done.
After the logs are uploaded successfully, you should see a notification letting you know that the log file processing completed successfully.
Then under Cloud Discovery, select Snapshot reports, and select your snapshot report.
In settings —Cloud Apps —automatic log upload you can see how create and manage organization’s data sources and log collector.
The Log collector can successfully handle log capacity of up to 50 GB per hour. The main bottlenecks in the log collection process are:
- Network bandwidth – Your network bandwidth determines the log upload speed.
- I/O performance of the virtual machine – Determines the speed at which logs are written to the log collector’s disk. The log collector has a built-in safety mechanism that monitors the rate at which logs arrive and compares it to the upload rate. In cases of congestion, the log collector starts to drop log files. If your setup typically exceeds 50 GB per hour, it’s recommended that you split the traffic between multiple log collectors.

You can also create log collector in easy way:
2.7. Discover and manage shadow IT
Use this process to roll out Shadow IT cloud discovery in your organization.
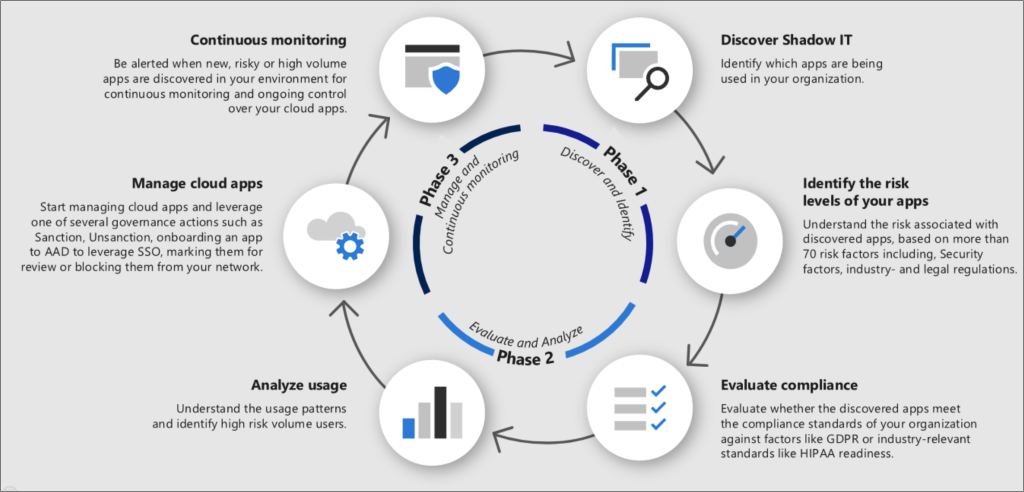
Phase 1: Discover and identify Shadow IT
Identify your organization’s security posture by running cloud discovery in your organization to see what’s actually happening in your network.
Identify the risk levels of your apps: Use the Defender for Cloud Apps catalog to dive deeper into the risks that are involved with each discovered app. The Defender for cloud app catalog includes over 31,000 apps that are assessed using over 90 risk factors.
Phase 2: Evaluate compliance and analyze: Check whether the apps are certified as compliant with your organization’s standards, such as HIPAA or SOC2.
Analyze usage: Now that you know whether or not you want the app to be used in your organization, you want to investigate how and who is using it. If it’s only used in a limited way in your organization maybe it’s ok, but maybe if the use is growing you want to be notified about it so you can decide if you want to block the app.
Phase 3: Manage your apps
Manage cloud apps: Defender for Cloud Apps helps you with the process for managing app use in your organization. After you identified the different patterns and behaviors used in your organization, you can create new custom app tags in order to classify each app according to its business status or justification. These tags can be then used for specific monitoring purposes, for example, identify high traffic that is going to apps that are tagged as risky cloud storage apps. App tags can be managed under Settings > Cloud Apps > Cloud Discovery > App tags.
Manage discovered apps using Microsoft Entra Gallery: Defender for Cloud Apps also uses its native integration with Microsoft Entra ID to enable you to manage your discovered apps in Microsoft Entra Gallery.
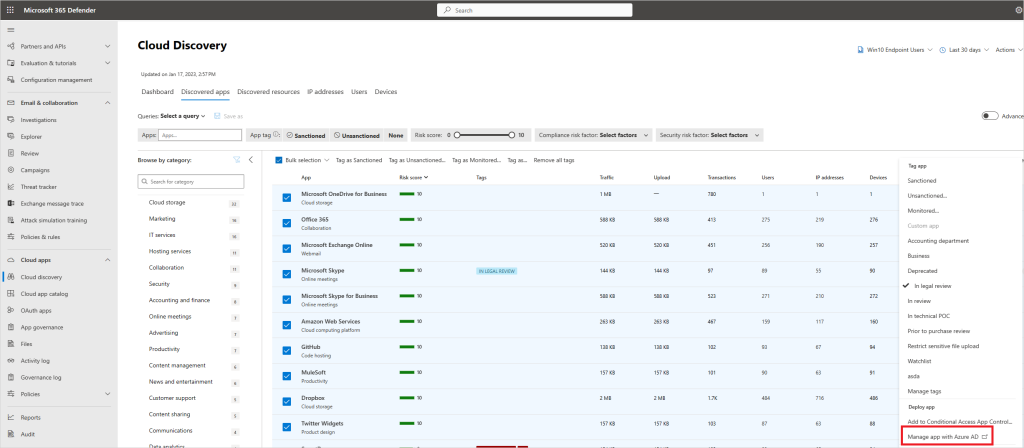
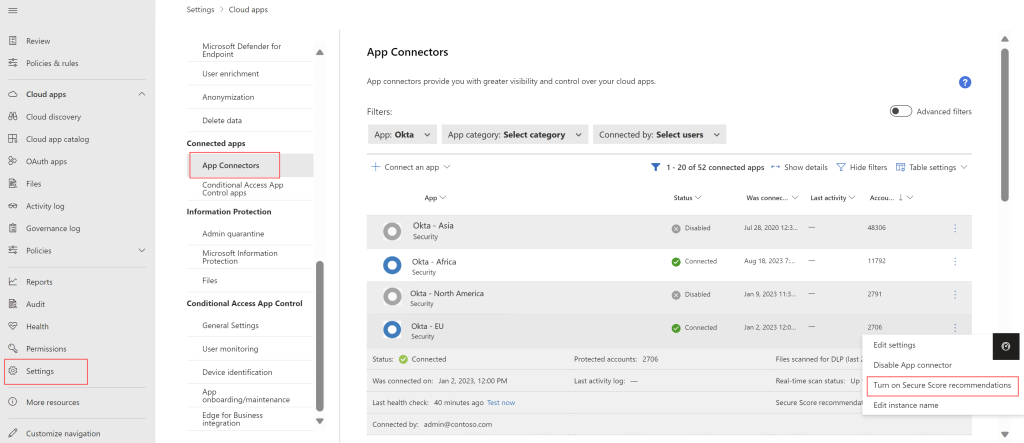
2.8. How to manage SaaS security posture
Your SaaS application environments may be configured in a risky posture. Microsoft Defender for Cloud Apps provides you with risk security configuration assessments for your SaaS applications to help you prevent possible risks.
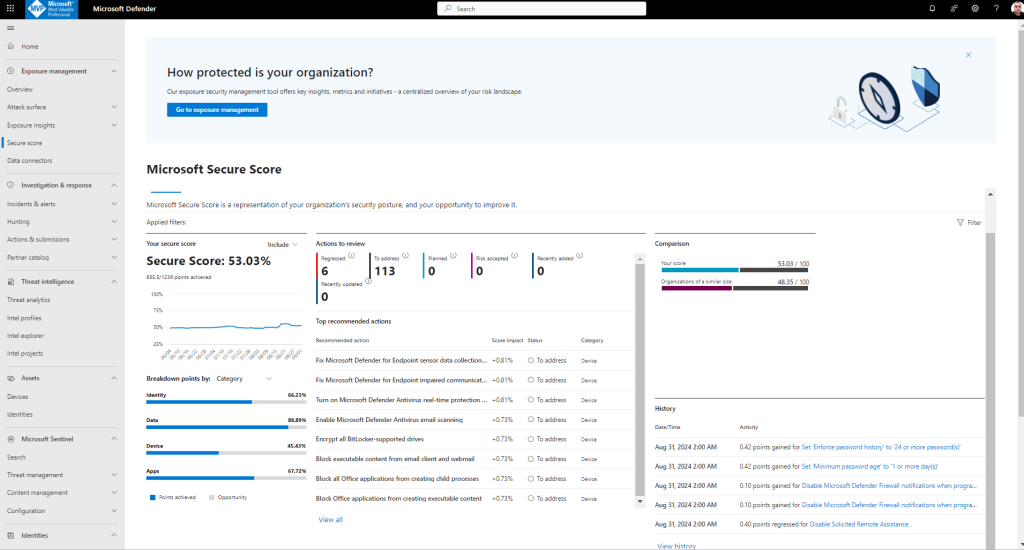
Actions you can take to improve your Microsoft Secure Score. Score updates may take up to 24 hours.
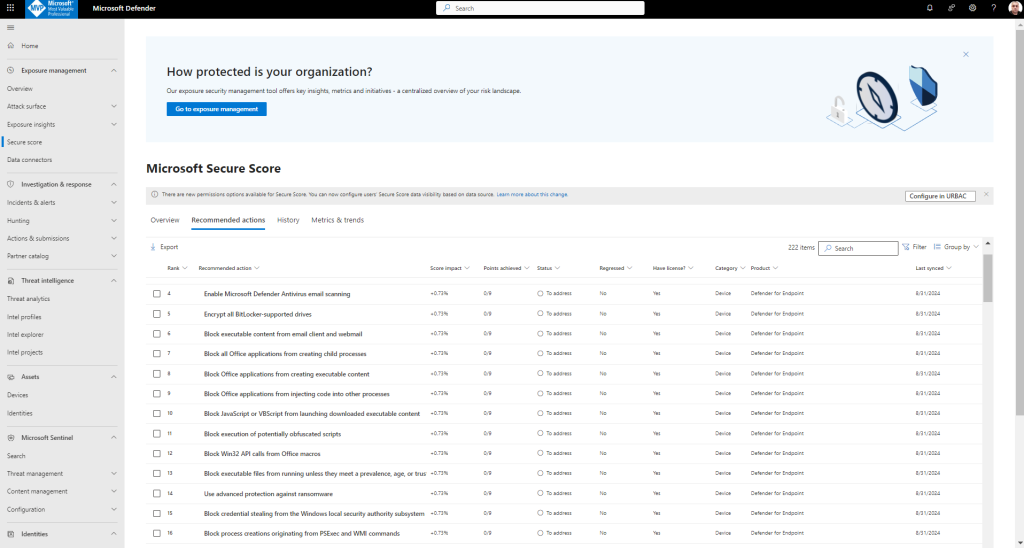
Turn on Secure Score recommendations!
This procedure describes how to ensure that your connector is set to show data in Microsoft Secure Score for SaaS app security posture management.
In Microsoft Defender XDR, select Settings > Cloud Apps > Connected apps > App Connectors.
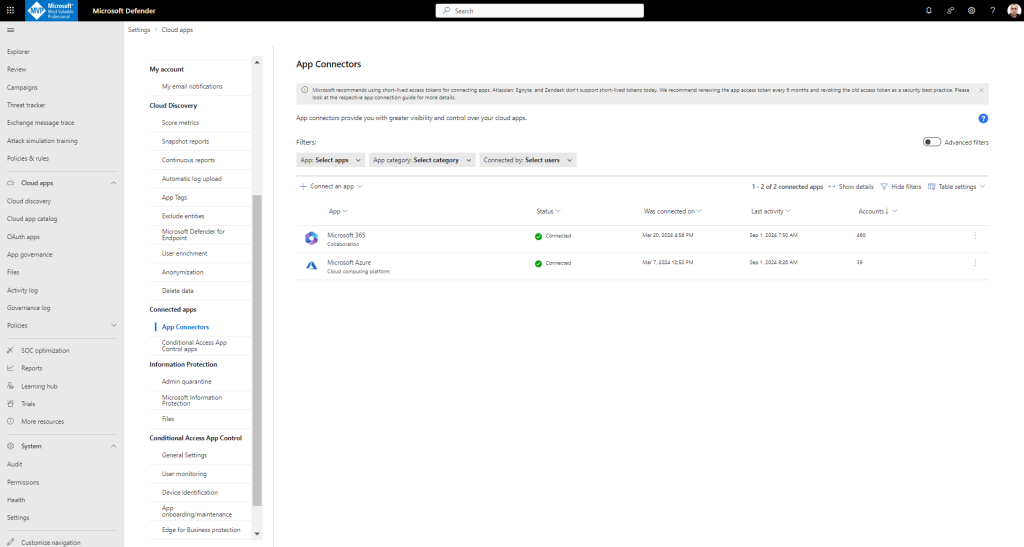
Use the filter to locate the app where you want to turn on Secure Score recommendations.
Open the instance drawer and note whether Secure Score recommendations are turned on or off.
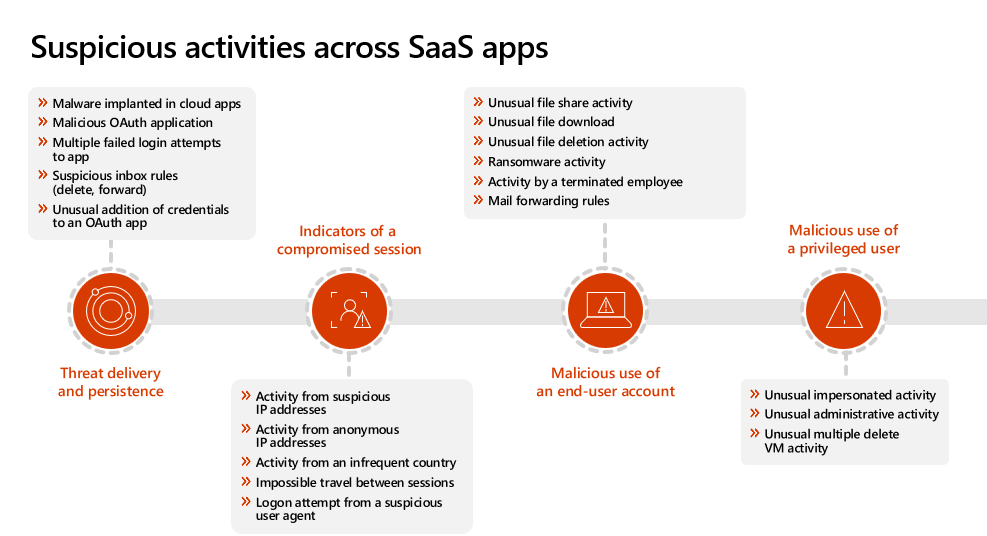
3. Threat protection with Defender for Cloud Apps
Across your cloud applications, persistence of malicious presence, compromised session alerts, end-user account misuse and malicious use of privileged user rights are all critical use cases to ensure your environment is fully equipped to handle.
Defender for Cloud Apps helps you mitigate different risks in the cloud. You can configure any policy and alert to be associated with one of the following risks:
- Access control: Continuously monitor behavior and detect anomalous activities, including high-risk insider and external attacks, and apply a policy to alert, block, or require identity verification for any app or specific action within an app. Enables on-premises and mobile access control policies based on user, device, and geography with coarse blocking and granular view, edit, and block. Detect suspicious login events, including multi-factor authentication failures, disabled account login failures, and impersonation events.
- Compliance: Catalog and identify sensitive or regulated data, including sharing permissions for each file, stored in file-sync services to ensure compliance with regulations such as PCI, SOX, and HIPAA
- Configuration control: Monitor configuration changes including remote configuration manipulation.
- Cloud discovery: Rate overall risk for each cloud app based on regulatory and industry certifications and best practices. Enables you to monitor the number of users, activities, traffic volume, and typical usage hours for each cloud application.
- DLP: Are proprietary files being shared publicly? Do you need to quarantine files?On-premises DLP integration provides integration and closed-loop remediation with existing on-premises DLP solutions.
- Privileged accounts: Real-time activity monitoring and reporting of privileged users and admins.
- Sharing control: Inspect the content of files and content in the cloud, and enforce internal and external sharing policies. Monitor collaboration and enforce sharing policies, such as blocking files from being shared outside your organization.
- Threat detection: Receive real-time notifications for any policy violation or activity threshold via email. By applying machine learning algorithms, Defender for Cloud Apps enables you to detect behavior that could indicate that a user is misusing data.
3.1. Control cloud apps with policies
Policies allow you to define the way you want your users to behave in the cloud. They enable you to detect risky behavior, violations, or suspicious data points and activities in your cloud environment. If necessary, you can integrate remediation work flows to achieve complete risk mitigation. There are multiple types of policies that correlate to the different types of information you want to gather about your cloud environment and the types of remediation actions you may want to take.
When you look at the Policy management page, the various policies and templates can be distinguished by type and icon to see which policies are available. The policies can be viewed together on the All policies tab, or in their respective category tabs:
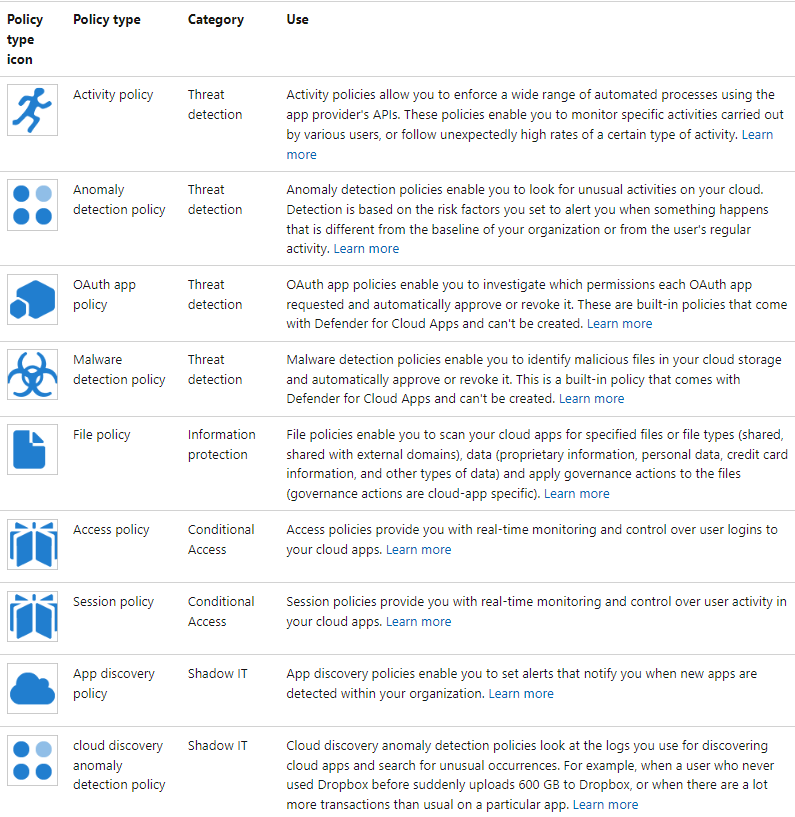
You can control risk follow this process to control risk with policies:
1.Create a policy from a template or a query.
2. Fine-tune the policy to achieve expected results.
3. Add automated actions to respond and remediate risks automatically.
4. You can either use the Defender for Cloud Apps policy templates as a basis for all your policies, or create policies from a query.
Policy templates help you set the correct filters and configurations necessary to detect specific events of interest within your environment. The templates include policies of all types, and can apply to various services.
To create a policy from Policy templates, perform the following steps:
In the Microsoft Defender Portal, under Cloud Apps, go to Policies -> Policy templates.
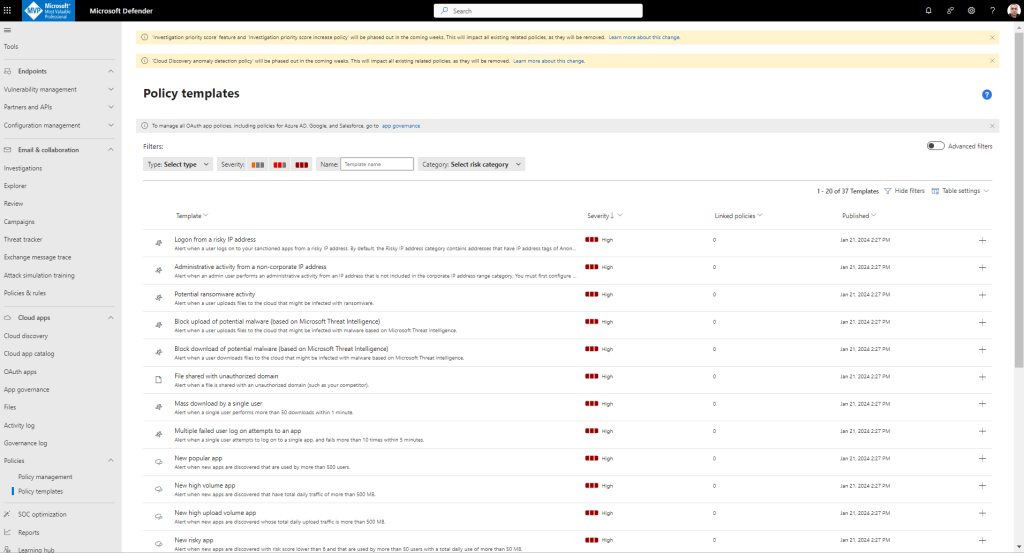
Select the plus sign (+) at the far right of the row of the template you want to use. A create policy page opens, with the pre-defined configuration of the template.
Modify the template as needed for your custom policy. Every property and field of this new template-based policy can be modified according to your needs.
After you create the new template-based policy, a link to the new policy appears in the Linked policies column in the policy template table next to the template from which the policy was created.
Defender for Cloud Apps lets you export a policies overview report showing aggregated alert metrics per policy to help you monitor, understand, and customize your policies to better protect your organization.
To export a log, perform the following steps:
1. In the Policies page, select the Export button.
2. Specify the required time range.
3. Select Export. This process may take some time.
4. After the report is ready, i n the Microsoft Defender Portal, go to Reports
and then Cloud Apps -> Exported reports.
4. App governance for OAuth apps
App governance in Defender for Cloud Apps is a set of security and policy management capabilities designed for OAuth-enabled apps registered on Microsoft Entra ID, Google, and Salesforce. App governance delivers visibility, remediation, and governance into how these apps and their users access, use, and share sensitive data in Microsoft 365 and other cloud platforms through actionable insights and automated policy alerts and actions.
If your organization satisfies the prerequisites, go to Microsoft Defender XDR > Settings > Cloud Apps > App governance and select Use app governance.
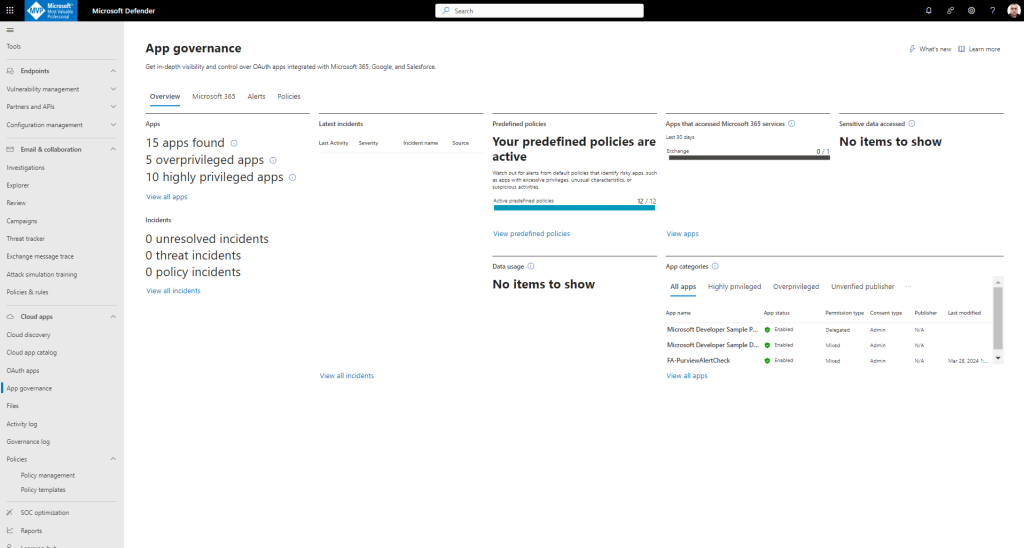
Get in-depth visibility and control over OAuth apps integrated with Microsoft 365, Google, and Salesforce.
You can also manage with OAuth apps, bulk extension and Create OAuth app policy:
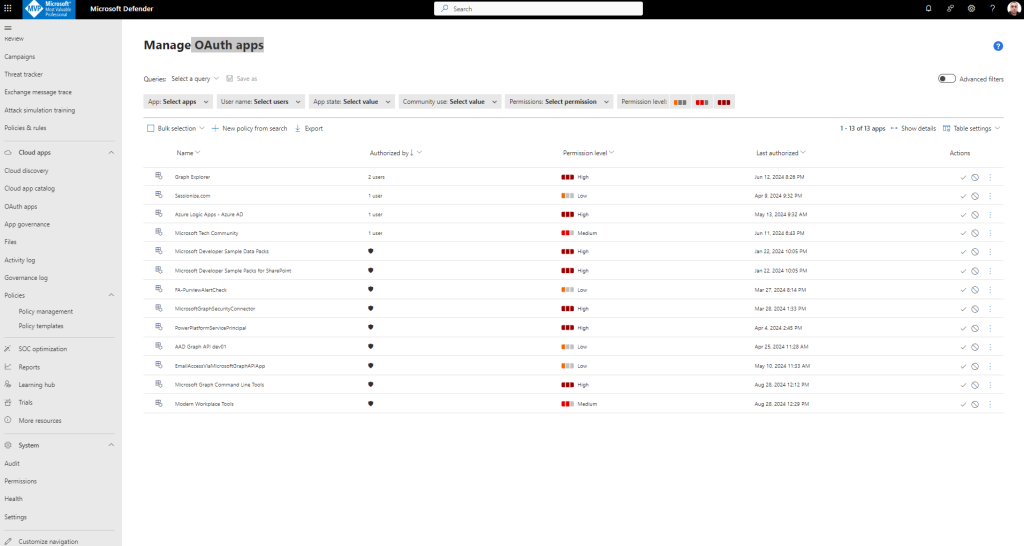
App governance also enables you to see which user-installed OAuth applications have access to data on Microsoft 365, Google Workspace, and Salesforce. It tells you what permissions the apps have and which users have granted access to their accounts.
App governance insights enable you to make informed decisions around blocking or restricting apps that present significant risk to your organization.
Insights: See a view of all non-Microsoft apps registered to Microsoft Entra ID, Google, or Salesforce in your organization on a single dashboard. You can see the status of apps and their activities, and react or respond to them.
Governance: Create proactive or reactive policies for app and user patterns and behaviors and protect your users from using noncompliant or malicious apps and limiting the access of risky apps to your data.
Detection: Be alerted and notified when there are anomalies in app activity and when noncompliant, malicious, or risky apps are used.
Remediation: Along with automatic remediation capabilities, use remediation controls in a timely manner to respond to anomalous app activity detections.
5. Best practices for protecting your organization with Defender for Cloud Apps
1. Discover and assess cloud apps
Integrating Defender for Cloud Apps with Microsoft Defender for Endpoint gives you the ability to use cloud discovery beyond your corporate network or secure web gateways. With the combined user and device information, you can identify risky users or devices, see what apps they are using, and investigate further in the Defender for Endpoint portal.
2. Enable Shadow IT Discovery using Defender for Endpoint
Cloud discovery analyzes traffic logs collected by Defender for Endpoint and assesses identified apps against the cloud app catalog to provide compliance and security information. By configuring cloud discovery, you gain visibility into cloud use, Shadow IT, and continuous monitoring of the unsanctioned apps being used by your users.
3. Discover and manage shadow IT in your network
Configure App Discovery policies to proactively identify risky, non-compliant, and trending apps
App Discovery policies make it easier to track of the significant discovered applications in your organization to help you manage these applications efficiently. Create policies to receive alerts when detecting new apps that are identified as either risky, non-compliant, trending, or high-volume.
4. Manage OAuth apps that are authorized by your users
Many users casually grant OAuth permissions to third-party apps to access their account information and, in doing so, inadvertently also give access to their data in other cloud apps. Usually, IT has no visibility into these apps making it difficult to weigh the security risk of an app against the productivity benefit that it provides.
5. Tag apps and export block scripts
After you’ve reviewed the list of discovered apps in your organization, you can secure your environment against unwanted app use. You can apply the Sanctioned tag to apps that are approved by your organization and the Unsanctioned tag to apps that are not. You can monitor unsanctioned apps using discovery filters or export a script to block unsanctioned apps using your on-premises security appliances. Using tags and export scripts allows you to organize your apps and protect your environment by only allow safe apps to be accessed.
6. Connect Microsoft 365
Connecting Microsoft 365 to Defender for Cloud Apps gives you immediate visibility into your users’ activities, files they are accessing, and provides governance actions for Microsoft 365, SharePoint, OneDrive, Teams, Power BI, Exchange, and Dynamics.
7. Connect your apps
Connecting your apps to Defender for Cloud Apps gives you improved insights into your users’ activities, threat detection, and governance capabilities. To see which third-party app APIs are supported, go to Connect apps.
8. Create policies to remove sharing with personal accounts
Connecting Microsoft 365 to Defender for Cloud Apps gives you immediate visibility into your users’ activities, files they are accessing, and provides governance actions for Microsoft 365, SharePoint, OneDrive, Teams, Power BI, Exchange, and Dynamics.
9. Integrating with Microsoft Purview Information Protection gives you the capability to automatically apply sensitivity labels and optionally add encryption protection. Once the integration is turned on, you can apply labels as a governance action, view files by classification, investigate files by classification level, and create granular policies to make sure classified files are being handled properly. If you do not turn on the integration, you cannot benefit from the ability to automatically scan, label, and encrypt files in the cloud.
10. Create data exposure policies
Use file policies to detect information sharing and scan for confidential information in your cloud apps.
11. Review reports in the Files page
Once you’ve connected various SaaS apps using app connectors, Defender for Cloud Apps scans files stored by these apps. In addition, each time a file is modified it is scanned again. You can use the Files page to understand and investigate the types of data being stored in your cloud apps. To help you investigate, you can filter by domains, groups, users, creation date, extension, file name and type, file ID, sensitivity label, and more.
12. Protect confidential data from being shared with external users
Create a file policy that detects when a user tries to share a file with the Confidential sensitivity label with someone external to your organization, and configure its governance action to remove external users. This policy ensures your confidential data doesn’t leave your organization and external users cannot gain access to it.
13. Block and protect download of sensitive data to unmanaged or risky devices
Use conditional access app control to set controls on your SaaS apps. You can create session policies to monitor your high risk, low trust sessions. Similarly, you can create session policies to block and protect downloads by users trying to access sensitive data from unmanaged or risky devices. If you don’t create session policies to monitor high-risk sessions, you’ll lose the ability to block and protect downloads in the web client, as well as the ability to monitor low-trust session both in Microsoft and third-party apps.