It’s time for a unified intelligent and comprehensive security operations platform for end-to-end threat detection, investigation, and response.
Now Microsoft Defender, XDR, Microsoft Sentinel, and Microsoft Security Copilot are available in public preview as a unified experience, all your alerts, incidents, playbooks, and policies in one place with more AI, more automation, and an unparalleled view of emerging threats enriching it all. One place to manage defenses. A single portal for your threat investigation, detection, and response. A single command center built on a common data model to help you manage your SOC and work faster. One place to investigate your incidents. Making incident triage more straightforward, investigation more seamless and insights more holistic. One place to search and hunt for threats across all your data. Simplified with help from Security Copilot, translating natural language to KQL. SIEM and XDR are truly better together with more comprehensive features like attack disruption which now extends from XDR to some data from the SIEM containing attacks quicker.
Microsoft’s unified security operations platform is now available in public preview. This comprehensive platform combines several essential security components to enhance security operations center (SOC):
1. Unified Capabilities:
This platform seamlessly integrates the full capabilities of:
- Cloud-native Security Information and Event Management (SIEM): Providing real-time monitoring, threat detection, and incident response.
- Extended Detection and Response (XDR): Enabling proactive threat hunting and rapid incident resolution.
- Generative AI Built for Cybersecurity: Leveraging artificial intelligence to enhance threat analysis and decision-making.
2. Unified Analyst Experience:
- Analysts in your SOC can now benefit from a truly unified experience.
- No more jumping between portals or sifting through low-level alerts.
- Focus on high-value tasks like remediating incidents and reducing attack surfaces.
3. Addressing Talent Gap:
- With a shortage of cybersecurity professionals, it’s crucial to optimize SOC workflows.
- The heart of the challenge lies in siloed data—too much information stored in too many places.
- This platform bridges those gaps by:
- Bringing data together.
- Normalizing and applying advanced analytics.
- Enriching insights with threat intelligence.
4. Unified Exposure Management:
- Last month, Microsoft added unified exposure management capabilities.
- These provide continuous, proactive visibility of assets and cyberattack paths.
- From prevention to detection and response, this platform equips security leaders and SOC teams with the tools they need.
- If you have a single Microsoft Sentinel workspace and at least one Defender XDR workload deployed, you can start using the unified experience in a production environment.
Had a great time at the CEE Cybersecurity Forum in Warsaw, Poland! I presented on the future of cybersecurity incident response with AI and the importance of Microsoft Unified, intelligent, and comprehensive security operations platform for end-to-end threat detection, investigation, and response.
https://cyber-security-forum.com/?utm_source=Linkedin&utm_medium=post&utm_campaign=cybersecurity-forum-25-4-2024#speakers
During my presentation and hands-on lab, I demonstrated the capabilities of Defender XDR, Microsoft Sentinel, and Security Copilot in a real attack scenario with AI-powered automation. These tools automatically disrupted the lateral movement of infected devices and suspended compromised accounts in real-time.

Microsoft’s unified security operations platform is now available in public preview. This comprehensive platform combines several essential security components to enhance security operations center (SOC):
1. Unified Capabilities, Unified Analyst Experience
This platform seamlessly integrates the full capabilities of:
- Cloud-native Security Information and Event Management (SIEM): Providing real-time. Monitoring, threat detection, and incident response.
- Extended Detection and Response (XDR): Enabling proactive threat hunting and rapid incident resolution.
- Generative AI Built for Cybersecurity: Leveraging artificial intelligence to enhance threat analysis and decision-making.
- Analysts in your SOC can now benefit from a truly unified experience.
- No more jumping between portals or sifting through low-level alerts.
- Focus on high-value tasks like remediating incidents and reducing attack surfaces.
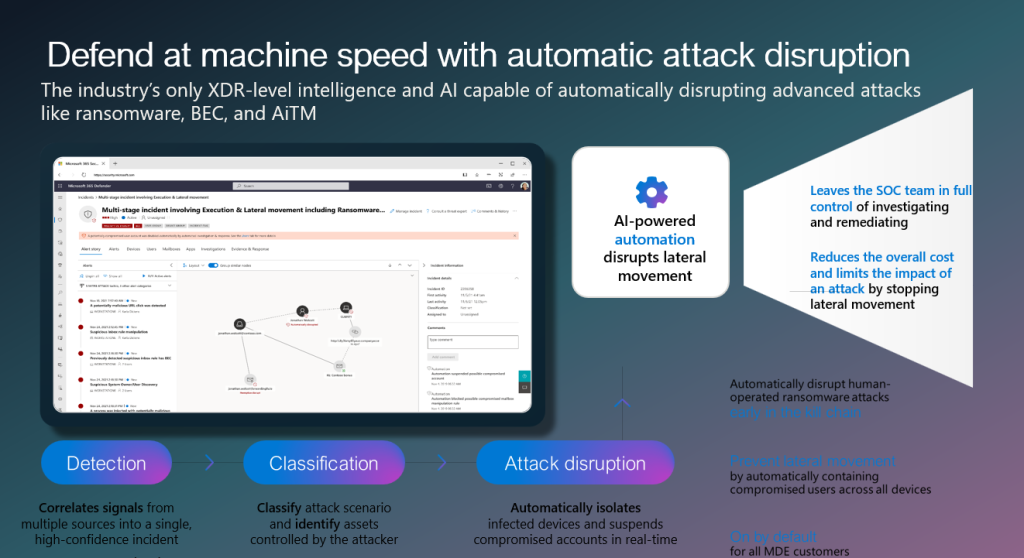

3. Addressing Talent Gap
- With a shortage of cybersecurity professionals, it’s crucial to optimize SOC workflows.
- The heart of the challenge lies in siloed data—too much information stored in too many places.
This platform bridges those gaps by:
- Bringing data together.
- Normalizing and applying advanced analytics.
- Enriching insights with threat intelligence.
4. Unified Exposure Management
- Last month, Microsoft added unified exposure management capabilities.
- These provide continuous, proactive visibility of assets and cyberattack paths.
- From prevention to detection and response, this platform equips security leaders and SOC teams with the tools they needű.
- If you have a single Microsoft Sentinel workspace and at least one Defender XDR workload deployed, you can start using the unified experience in a production environment.
5. Main Features
- Prevent breaches with end-to-end visibility of your attack surface.
- Shut down in-progress attacks with automatic attack disruption.
- Investigate and respond faster, customers saw up to an 80% reduction in incidents, with improved correlation of alerts to incidents across Microsoft Sentinel data sources, accelerating triage and response.
- Microsoft Copilot for Security helps security analysts accelerate their triage with comprehensive incident summaries that map to the MITRE framework, reverse-engineer malware, translate complex code to native language insights, and even complete multistage attack remediation actions with a single click.
- After your workspace is connected, the banner on the Overview page shows that your unified security information and event management (SIEM) and extended detection and response (XDR) is ready. The Overview page is updated with new sections that include metrics from Microsoft Sentinel like the number of data connectors and automation rules.
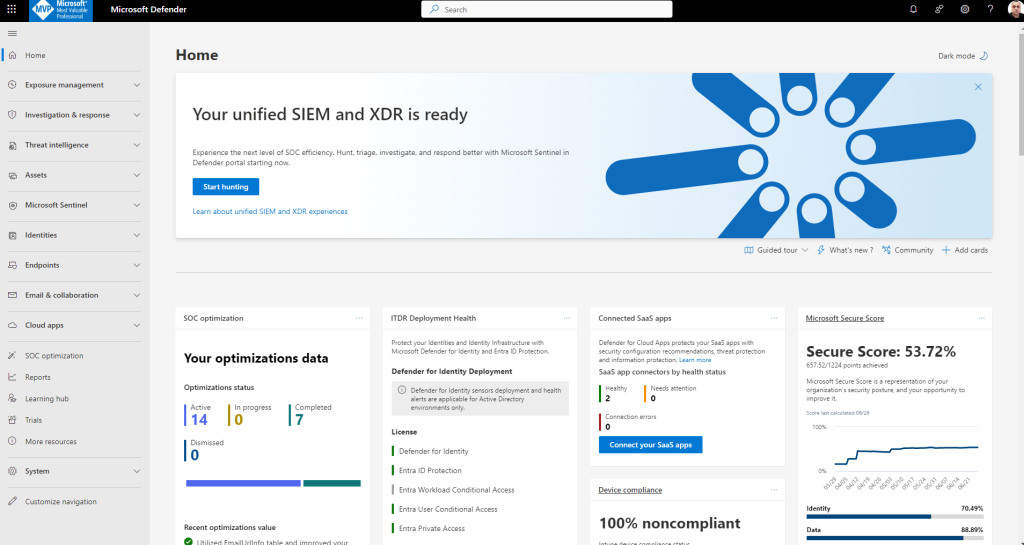
Key components Defender XDR:
Endpoints with Microsoft Defender for Endpoint – Microsoft Defender for Endpoint is a unified endpoint platform for preventative protection, post-breach detection, automated investigation, and response.
Assets with Defender Vulnerability Management – Microsoft Defender Vulnerability Management delivers continuous asset visibility, intelligent risk-based assessments, and built-in remediation tools to help your security and IT teams prioritize and address critical vulnerabilities and misconfigurations across your organization.
Email and collaboration with Microsoft Defender for Office 365 – Defender for Office 365 safeguards your organization against malicious threats posed by email messages, links (URLs), and collaboration tools.
Identities with Microsoft Defender for Identity – Microsoft Defender for Identity uses Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
Applications with Microsoft Defender for Cloud Apps – Microsoft Defender for Cloud Apps is a comprehensive cross-SaaS solution that brings deep visibility, strong data controls, and enhanced threat protection to your cloud apps.
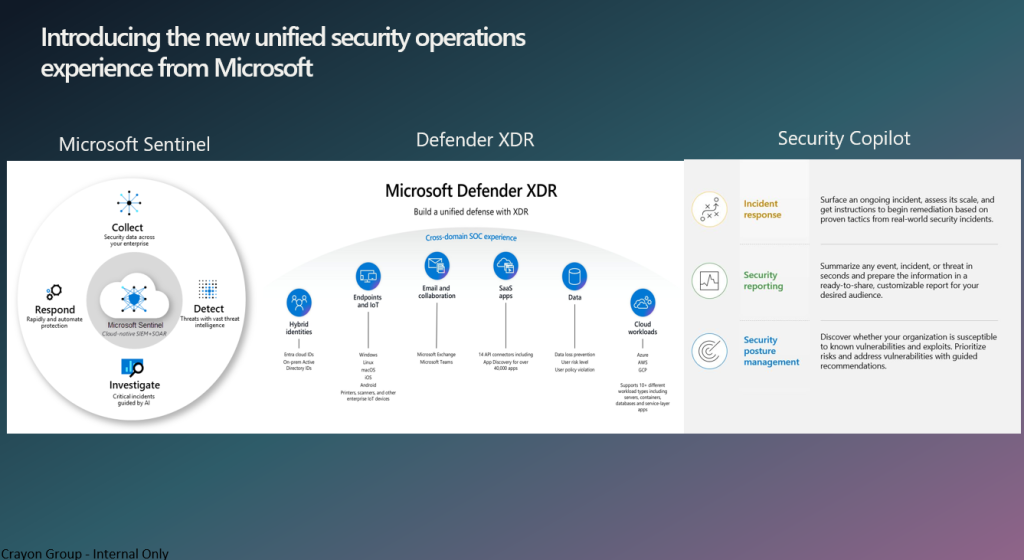
The unified security operations platform that combines Microsoft Defender XDR, Microsoft Sentinel, and Microsoft Security Copilot delivers a powerful solution for security teams. Here’s how it significantly reduces investigation time and enables faster work:
Unified Incident Experience:
By bringing together these three components, security analysts gain a streamlined incident experience. They can seamlessly triage incidents, view threats across the entire digital estate, and respond effectively.
Reduced Tool Switching:
Microsoft Sentinel is now integrated into the Defender portal, eliminating the need for constant tool switching. Analysts can focus on context-driven investigations, expedite incident response, and prevent breaches more efficiently.
Single Data Model:
The unified platform operates with a single data model, ensuring consistency and coherence across all security operations. This simplifies data exploration and management, saving valuable time3.
Advanced Hunting and Incident Management:
Security Copilot enhances advanced hunting capabilities. Analysts can write queries in natural language, accelerating complex investigations. Additionally, incident management becomes more efficient within this unified environment.
AI and Automation:
The platform is enhanced with AI and automation. Security Copilot leverages generative AI to understand attacks, analyze files, and recommend appropriate mitigation measures. This swift assessment speeds up incident resolution
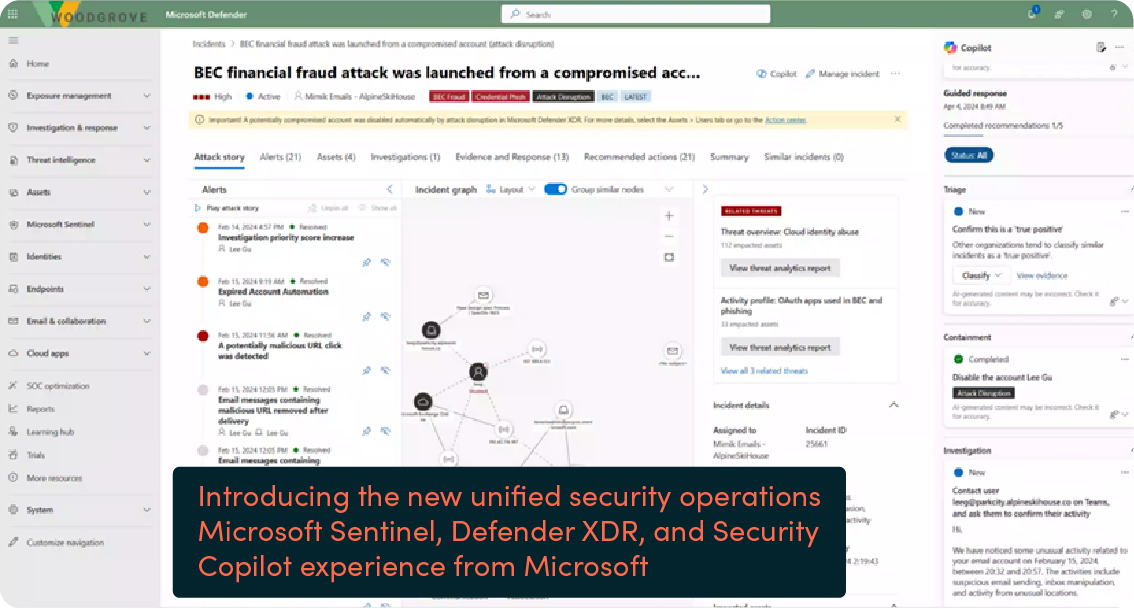
Introducing the new unified security operations Microsoft Sentinel, Defender XDR, and Security Copilot experience from Microsoft

👉 Download the ebook: https://lnkd.in/d2sV7HrT